VPN Essentials
VPN technology leverages a variety of protocols and algorithms to provide information security services. In VPN architectures, confidentiality is maintained by encrypting the packet, integrity is guaranteed by validating the hash function, and availability to authorized users is confirmed by matching the secret keys. Figure 19-1 shows three main components of information security—confidentiality, integrity, and availability, which is known as the CIA triad.
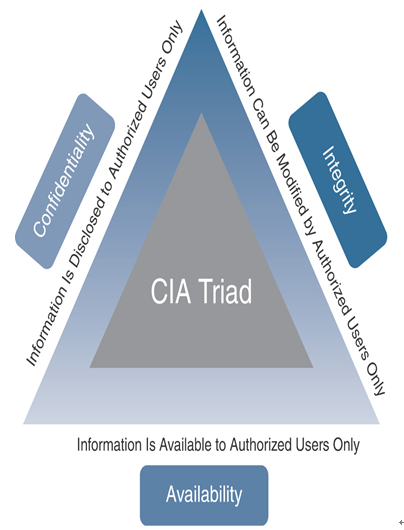
Figure 19-1 CIA Triad Information Security Model
You can enable VPN services on many modern networking platforms, such as a router, a firewall, and even on the public cloud. When it is enabled, the platform builds a secure tunnel over the Internet, encapsulates the packets from your private network, and sends them through that secure tunnel. Likewise, on the other end of the secure tunnel, another VPN-enabled device receives the packets, decapsulates them, and sends them to a destination endpoint that is located at another private network. Regardless of the platform you deploy, the VPN architectures are mainly two types:
- Site-to-Site VPN (S2S VPN)
- Remote Access VPN (RAVPN)
Figure 19-2 shows the processing of packets through the VPN components of Secure Firewall.
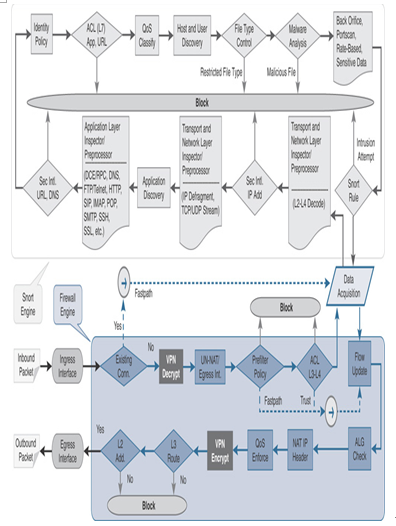
Figure 19-2 Processing of Packets by Various Components of Security Engines (Highlighting VPN Operations)
Site-to-Site VPN
In a site-to-site virtual private network, the VPN gateways located in geographically separated networks connect each other via a secure tunnel over the Internet. This connection makes all the hosts in participating sites a part of the same virtual network. This network enables the hosts to connect to each other through a secure tunnel built by their respective gateways. You can configure a threat defense to act as a VPN gateway. Secure Firewall can support three types of site-to-site VPN topologies:
- Point-to-Point: Two VPN gateways are connected via a secure tunnel.
- Hub and Spoke: A VPN gateway (hub) connects to multiple VPN gateways (spoke nodes) via independent secure tunnels.
- Full Mesh: VPN gateways in a group connect to each other via multiple secure tunnels.
Figure 19-3 shows a high-level design of a site-to-site virtual private network with point-to-point topology.
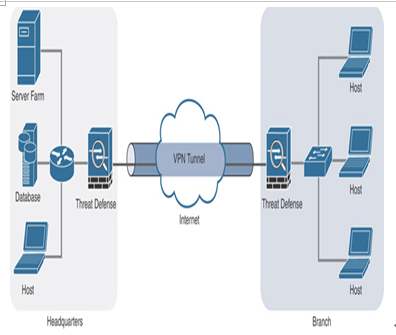
Figure 19-3 Site-to-Site VPN: Point-to-Point Topology
Figure 19-4 shows a high-level design of a site-to-site virtual private network with hub-and-spoke topology.
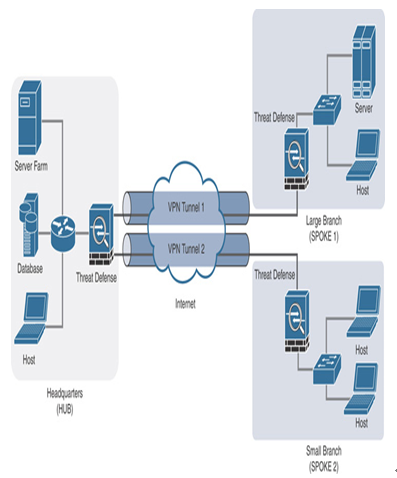
Figure 19-4 Site-to-Site VPN: Hub-and-Spoke Topology
Figure 19-5 shows a high-level design of a site-to-site virtual private network with full mesh topology.
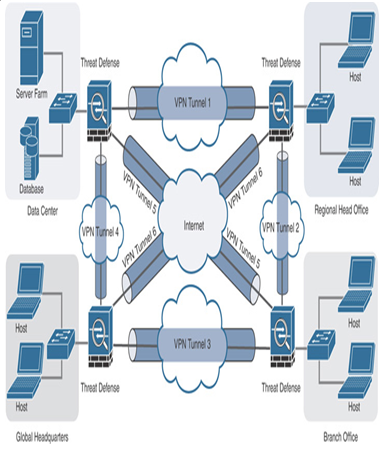
Figure 19-5 Site-to-Site VPN: Full Mesh Topology
Leave a Reply