Enable Logging on Access Control Policy
In the preceding section, you added a syslog server in the platform settings policy. Next, you need to instruct Secure Firewall to send log messages to the syslog server configured in the policy. You can configure an access control policy to send syslog messages for intrusion events and file and malware events. This method of producing syslog events from the access control policy is global and simple to configure. After you open the desired access control policy in the policy editor, go to the Logging tab and select the check boxes as shown in Figure 21-12. Make sure to save the changes on the access control policy. Finally, deploy the policy to your threat defense device by navigating to Deploy > Deployment.
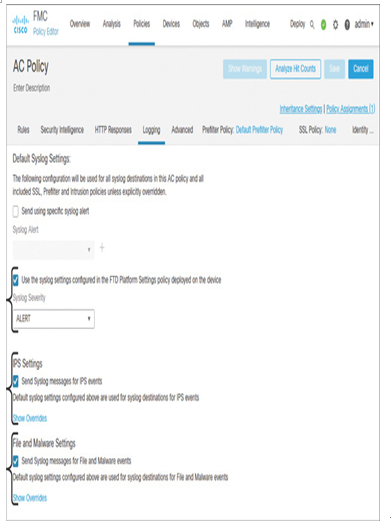
Figure 21-12 Enable Logging Globally for Intrusion and File Events
Verification
After the policy has been successfully deployed, you can perform the following tests:
- Use the browser of your internal end-user computer and attempt to download an executable (.exe) file from the web server. The threat defense device should block the download attempt, and the management center should display a file event.
- Use the CLI of the end-user computer to connect to the web server over the Telnet protocol. If you enter incorrect credentials, the threat defense device should block the login attempt, and the management center should display an intrusion event.
For both blocked attempts, the threat defense device should also send syslog messages to the syslog server (Figure 21-13 shows an example). Note that both messages are originated from the threat defense device (Syslog device ID/hostname: ThreatDefense, Originator IP address 10.1.1.71).
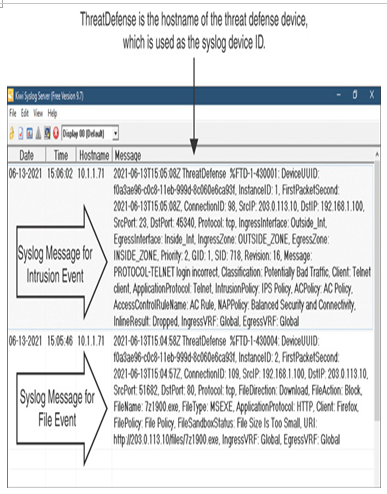
Figure 21-13 Syslog Server Showing Messages for Intrusion and File Events
Sending Syslog from Management Center
The previous sections described how to use the platform settings policy to enable a threat defense device to send messages directly to a syslog server. In the following sections, you learn how to enable a management center to send log messages directly to a syslog server. If a threat defense device detects and blocks malicious file transfers or intrusion attempts, sending syslog messages directly from the threat defense would be the optimal choice. However, if you want to receive syslog messages for the events that need to be processed and correlated by the management center, you should configure the management center to send syslog alerts directly.
Create Syslog Alerts
The following steps show how to generate syslog events from the management center:
Step 1. On the management center, go to Policies > Actions > Alerts. The Alerts page appears.
Step 2. On the Alerts tab, click the Create Alert drop-down menu and select Create Syslog Alert (see Figure 21-14). The Edit Syslog Alert Configuration window opens.
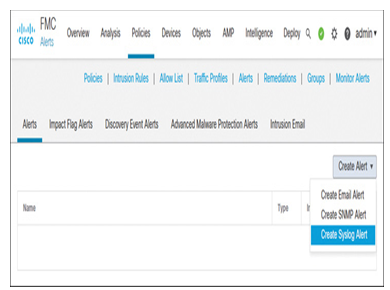
Figure 21-14 Navigating to the Syslog Alerts Creation Menu
Step 3. In the configuration window, name the configuration and enter the relevant information of the syslog server you wish to use. Secure Firewall uses the IP address and port number you enter in this window to communicate with the syslog server.
Step 4. Choose a facility and severity levels as described in Table 21-3 and Table 21-4. Optionally, provide a unique tag to distinguish any messages from the management center to the syslog server. Figure 21-15 shows an example of syslog alert configuration.
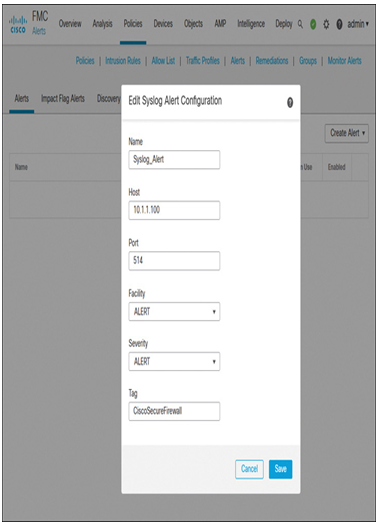
Figure 21-15 Syslog Alert Configuration Example
Step 5. Click Save to save the configuration. The GUI returns to the Alerts tab. Make sure the newly created alerting system is enabled.
Step 6. At this stage, you can choose the types of events for which you want to receive alerts on the syslog server. For example, you can enable the syslog notification for all event types under the Impact Flag Alerts and Discovery Event Alerts tabs, as shown in Figure 21-16 and Figure 21-17. Note that, to trigger these alerts, the management center requires an active Network Discovery policy (Network Discovery is described in detail in Chapter 9, “Network Discovery Policy”).
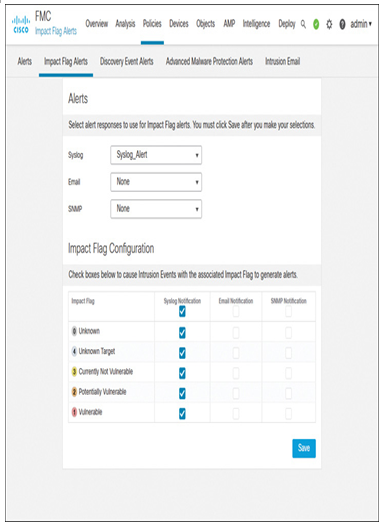
Figure 21-16 Enabling Syslog Notifications for Impact Flag Alerts
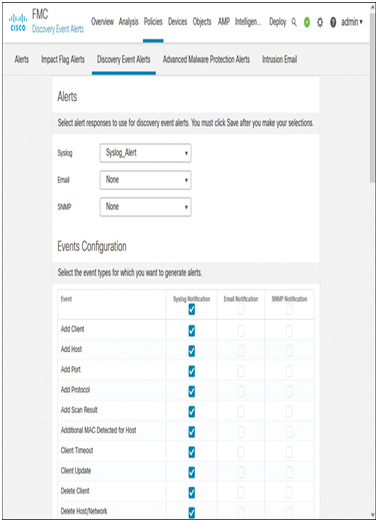
Figure 21-17 Enabling Syslog Notifications for Discovery Event Alerts
Step 7. Make sure to use the Save button to save any configuration changes.
Leave a Reply