Verification
After you successfully deploy a QoS policy, you can verify the deployment status from the threat defense CLI. Example 20-1 shows confirmation of the QoS policy configurations and the interface where the policy is deployed.
Example 20-1 Policy Map Showing the Active QoS Policy on an Interface
! To view the rate-limiting settings:
>
show running-config policy-map
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map type inspect ip-options UM_STATIC_IP_OPTIONS_MAP
parameters
eool action allow
nop action allow
router-alert action allow
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect icmp
inspect icmp error
inspect snmp
inspect ip-options UM_STATIC_IP_OPTIONS_MAP
class class_snmp
inspect snmp
class class-default
set connection advanced-options UM_STATIC_TCP_MAP
policy-map
policy_map_INSIDE_INTERFACE
match flow-rule
qos 268462080
police input 8000000 250000
police output 40000000 1250000
!
>
! To determine where a policy is applied:
>
show running-config service-policy
service-policy global_policy global
service-policy
policy_map_INSIDE_INTERFACE
interface INSIDE_INTERFACE
>
Now, you can verify the impact of the QoS policy you have deployed. First, download a file from the server to a client system. Then upload a file from the client PC to the server. You should notice two different traffic rates.
Figure 20-14 shows a simple lab topology that you can use to limit and verify the download and upload speeds through a threat defense.
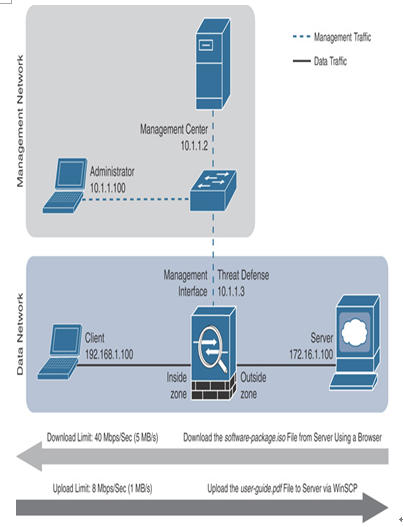
Figure 20-14 Lab Topology to Test the Rate-Limiting of Traffic Through a Threat Defense
Figure 20-15 shows the download of a software image file. The threat defense enforces the download rate up to 5 MB/sec, per the QoS policy.
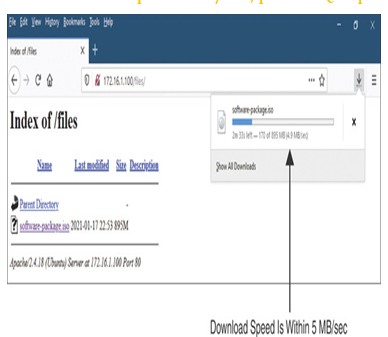
Figure 20-15 Compliance of the Download Rate (Defined in the QoS Policy)
Figure 20-16 shows the upload of a PDF file. The threat defense regulates the upload rate below 1 MB/sec, per the QoS policy.
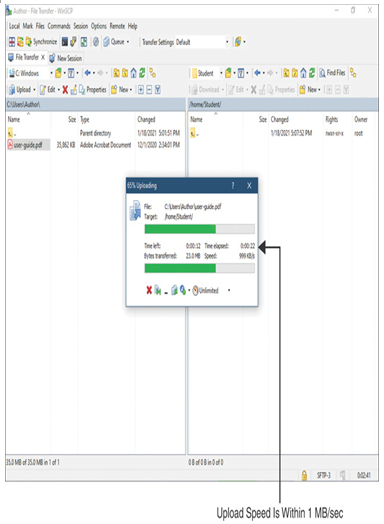
Figure 20-16 Compliance of the Upload Rate (Defined in the QoS Policy)
Both of these transfers—download of the ISO and upload of the PDF—are initiated by a host that is located at the inside zone. Therefore, the traffic matches the QoS rule, and the threat defense regulates the traffic rate. However, if the connection is initiated by an outside system, it does not match the QoS rule condition. Hence, the QoS policy does not limit the traffic rate; the source and destination hosts should be able to utilize the full capacity of the threat defense interface bandwidth.
Leave a Reply