Configuring QoS Policy
Follow these steps to create a QoS policy and add a rule within it:
Step 1. Navigate to Devices > QoS. Secure Firewall does not come with a default QoS policy, so click the New Policy button to create one (see Figure 20-7). The New Policy window appears.
Figure 20-7 Home Page for the QoS Policy
Step 2. Name the new policy and add a target device to which you want to apply this policy. Click Save to save the changes. The QoS policy editor page appears.
Step 3. Select a device for the new QoS policy you want to create and click Add to Policy (see Figure 20-8). Then click Save.
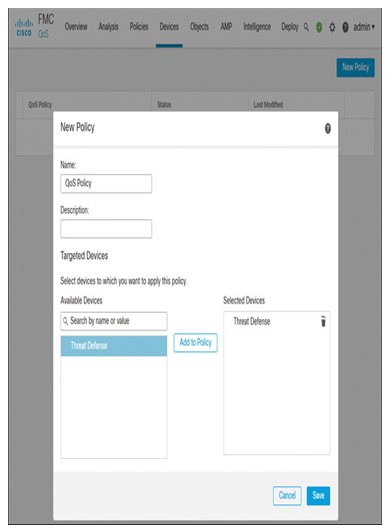
Figure 20-8 Assigning a QoS Policy to a Threat Defense
Step 4. On the QoS policy editor page, notice that there is a link to the Policy Assignments option that you can use to associate a new managed device with this policy. Click the Add Rule button (see Figure 20-9). The Add Rule window appears, and in it you can define a rule condition.
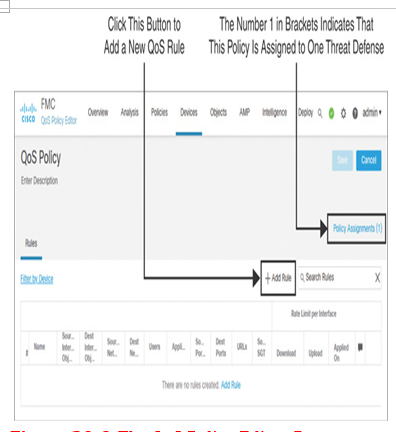
Figure 20-9 The QoS Policy Editor Page
Step 5. Name the new QoS rule. Using the Apply QoS On drop-down, define where you want to rate-limit traffic. In addition, on the Interface Objects tab, add a source and destination interface to the rule condition.
Tip
You should rate-limit traffic as close to the source as possible to ensure that the traffic rate does not go beyond an entitled limit throughout the network.
Figure 20-10 shows a new QoS rule, named QoS Rule, that is applied on Interfaces in Source Interface Objects. This rule limits traffic rates only when the traffic originates from the Inside_Zone interface and is destined for the Outside_Zone.
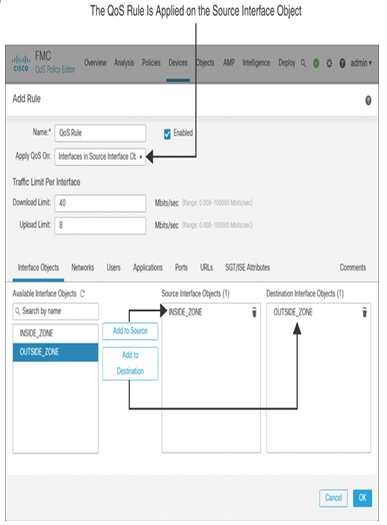
Figure 20-10 Selecting Interface Objects in a Rule
Step 6. Enter a desired traffic limit for the interface. You can provide upload and download limits separately. If you do not enter a value, the threat defense enables the maximum throughput for that physical interface.
Table 20-2 provides a conversion chart for commonly used traffic rates. When you enter a traffic limit, the threat defense considers the value as megabits per second (Mbps), not megabytes per second (MB/sec). The highlighted rows of this table are used in the configuration example in this chapter.
Table 20-2 Megabits per Second to Megabytes per Second Conversion Table
| Megabits per Second (Mbps) | Megabytes per Second (MB/sec) |
| 1 Mbps | 0.125 MB/sec |
| 4 Mbps | 0.5 MB/sec |
| 8 Mbps | 1 MB/sec |
| 10 Mbps | 1.25 MB/sec |
| 16 Mbps | 2 MB/sec |
| 40 Mbps | 5 MB/sec |
| 80 Mbps | 10 MB/sec |
| 100 Mbps | 12.5 MB/sec |
Note
A threat defense supports the rate limit of 0.008 to 100,000 Mbps per interface. If you want to allocate below 0.008 Mbps to any hosts, it implies that those hosts are not important to you. You may just want to consider blocking them by using an access rule or a prefilter rule.
Figure 20-11 shows the traffic limits for download and upload flows, 40 Mbps and 8 Mbps, respectively.
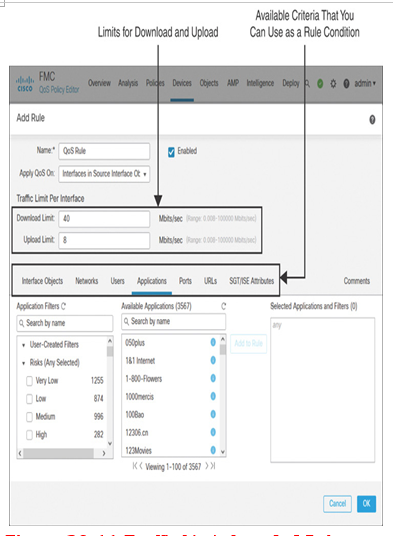
Figure 20-11 Traffic Limit for a QoS Rule
Step 7. Optionally, add a precise rate-limiting condition based on any additional networking characteristics, such as network address, port number, application, URL, and user identity.
Step 8. After you outline a rule condition, click the OK button to create the QoS rule. The browser returns to the QoS policy editor page. Click the Save button to preserve the QoS rules you have created.
Figure 20-12 shows the custom QoS rule you just created.
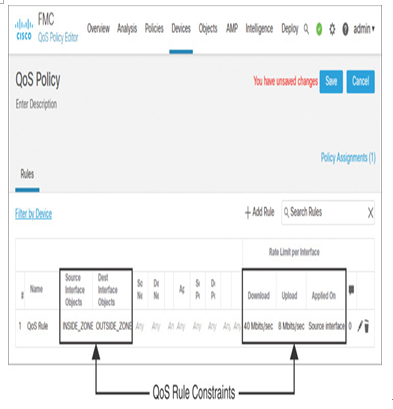
Figure 20-12 Viewing Available QoS Rules on the QoS Policy Editor Page
At this point, you can go to Deploy > Deployment to activate a QoS rule, but by default, the threat defense does not generate any log when it triggers a QoS rule. A QoS policy does not offer an option for logging. If you want to view QoS-related statistics for any specific connection, you must identify the associated access rule that triggers the QoS rule and enable logging at the end of that connection. To accomplish that, you have to edit the access control policy and redeploy the revised policy.
Figure 20-13 shows the option to enable logging for traffic matching the default action. Because this exercise does not use any custom access rules, you can enable logging for the default action to generate QoS data when a connection hits the default action.
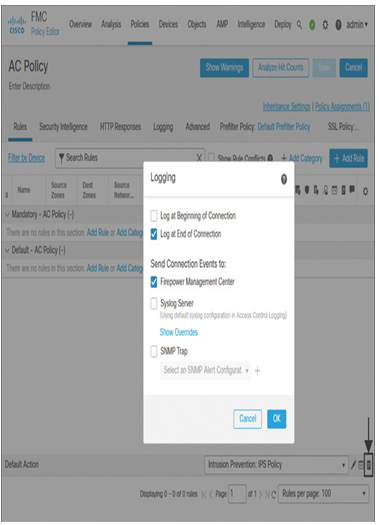
Figure 20-13 Enabling Logging for the Default Action of an Access Control Policy
Leave a Reply