Quality of Service Essentials
There are multiple ways to enable quality of service (QoS) in a network. A threat defense implements the traffic policing mechanism to limit the rate of traffic. With this method, the threat defense drops excessive traffic when the traffic rate reaches a predefined limit. As of this writing, the threat defense does not support traffic shaping, where excessive traffic is queued in a buffer—rather than being dropped—for later transmission.
Figure 20-1 illustrates the crests and troughs of the traffic pattern when a threat defense rate-limits traffic using the policing method.
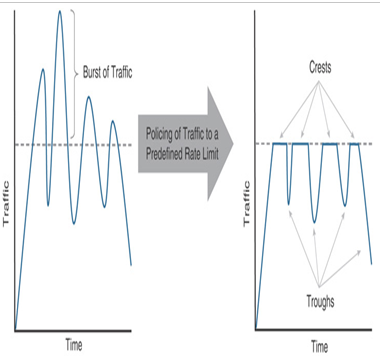
Figure 20-1 Traffic Policing Method Dropping Excessive Traffic
Figure 20-2 shows a typical graph illustrating traffic that is rate-limited by the shaping mechanism.
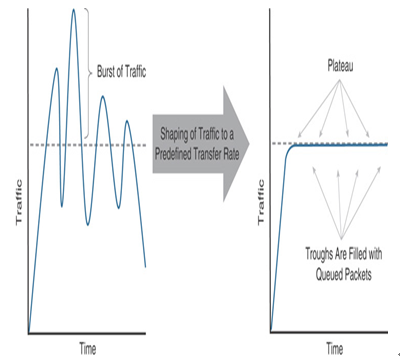
Figure 20-2 Traffic Shaping Queues Excessive Traffic for Later Transmission
You can activate only one QoS policy on a threat defense at any given time. However, you can add multiple QoS rules within a single QoS policy. Each QoS rule must be associated with a source interface and a destination interface, where both of them have to be routed interfaces. You can set separate upload and download speed limits for the traffic that matches the conditions of a QoS rule. Furthermore, you can define the QoS rule conditions based on advanced networking characteristics, such as network address, port number, application, URL, and user identity.
The Snort engine evaluates a QoS rule and classifies traffic. When a packet matches with a QoS rule, the Snort engine sends the ID of the matching rule to the firewall engine. The firewall engine limits the rate of individual flows based on the download and upload speed limits defined on the QoS rule. You must enable logging at the end of a connection to view QoS-related information.
Figure 20-3 shows the workflow of QoS implementation on Secure Firewall. You use the management center to configure and apply a QoS policy and view any QoS events. The threat defense ensures that the traffic conforms to the QoS rule. Figure 20-4 highlights the operations of a QoS policy in a threat defense architecture.
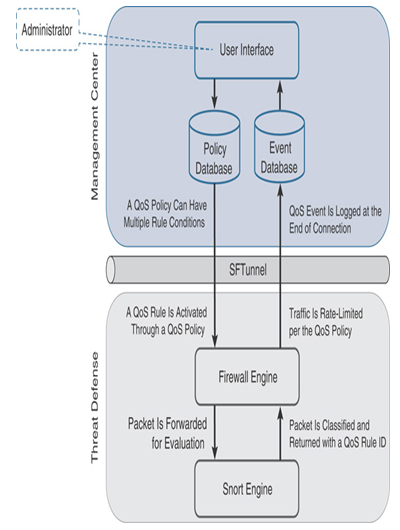
Figure 20-3 QoS Implementation on the Secure Firewall
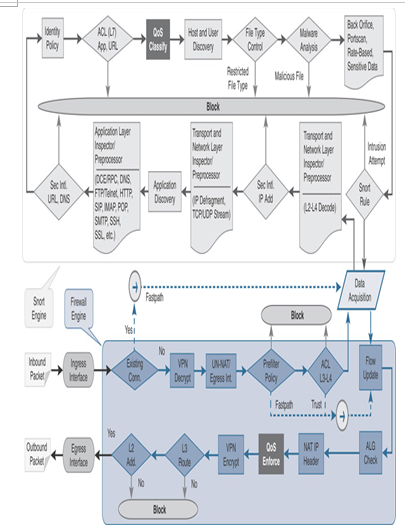
Figure 20-4 Processing of Packets by Various Components of Security Engines (Highlighting QoS Operations)
Best Practices for Enabling QoS
As of this writing, Secure Firewall supports up to 32 QoS rules within a single QoS policy. You can add different rule conditions for different network segments that are connected to different threat defense interfaces. However, when you want to implement a QoS policy, you should position the threat defense as close to the source as possible to ensure that the traffic does not consume the network and system resources more than it should.
Figure 20-5 shows a typical network where the threat defense enables different QoS rules through the same QoS policy. Traffic is originated from different source networks and rate-limited by different QoS rules.
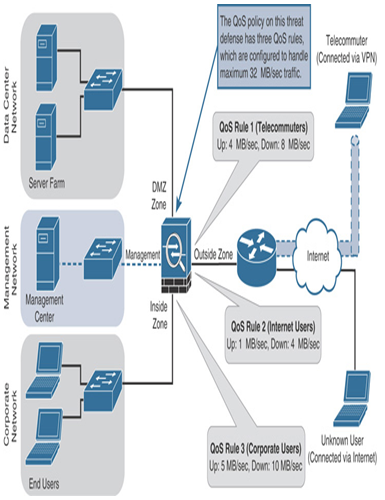
Figure 20-5 Different QoS Rules Can Be Applied to Different Types of Users
Leave a Reply