Sending Syslog from Threat Defense
By using the platform settings policy, you can deploy different logging configurations to different threat defense devices. The platform settings policy allows you to configure many device-specific options in one place and then deploy them to one or more threat defense devices as needed. For example, you can add a custom banner to appear during a threat defense login; allow the hosts that can communicate with a threat defense over SSH, HTTPS, and ICMP protocols; define how the threat defense device will synchronize time with its management center or an NTP server; provide health monitoring status over the Simple Network Management Protocol (SNMP); send security events and system messages to an external syslog server in addition to other configurations and settings.
The platform settings configuration page presents many granular settings for syslog. The following configuration example uses minimal steps to enable syslog. To learn about every option in the platform settings, read the official user guide available at cisco.com.
Add a Syslog Server on Platform Settings
To add a syslog server on Secure Firewall using the platform settings policy, follow these steps:
Step 1. Navigate to Devices > Platform Settings. Click the New Policy button and select Threat Defense Settings, as shown in Figure 21-6.
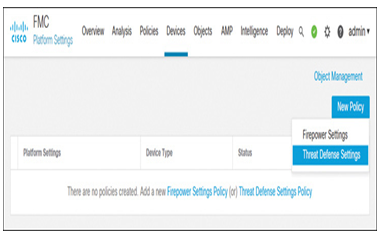
Figure 21-6 Navigating to the Platform Settings Page for a Threat Defense
Step 2. On the New Policy window, name the policy, add your threat defense to it, and click the Save button to save the policy (see Figure 21-7). The platform settings configuration page appears.
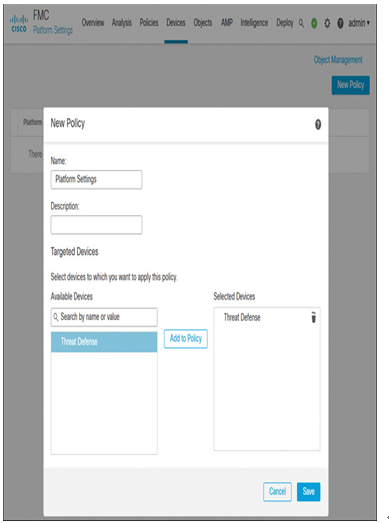
Figure 21-7 Creating a New Policy for Threat Defense Platform Settings
Step 3. On the left panel of the platform settings configuration page, click Syslog. The syslog configuration page appears.
Step 4. Under the Logging Setup tab, select Enable Logging, as shown in Figure 21-8. You can leave the remaining options on this tab unchecked because they are optional for this lab exercise.
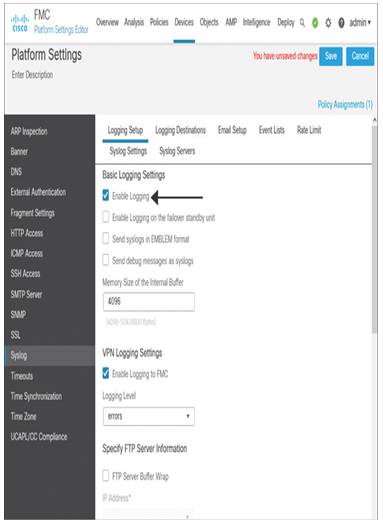
Figure 21-8 Syslog Configuration Page Showing the Logging Setup Tab
Step 5. Navigate to the Syslog Servers tab and click Add. It opens the Add Syslog Server window. Enter the syslog server IP address, transport protocol, and port number. Because the syslog server in this lab environment is deployed in the management network, select the Device Management Interface for its reachability. Click OK. Now the tab should look like the one shown in Figure 21-9.
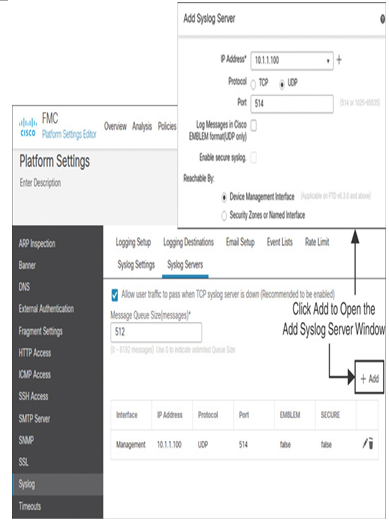
Figure 21-9 Syslog Configuration Page Showing the Syslog Servers Tab
Step 6. At this stage, you could save the platform settings configurations and move to the next section. However, if you would like to enhance the syslog messaging, you can enable additional options. For example, you can insert a timestamp and an originator device ID into the syslog messages (see Figure 21-10). Likewise, you can enable various fine-tuning features, such as rate limiting of syslog messages based on syslog ID or their severity levels, to improve Secure Firewall performance (see Figure 21-11).
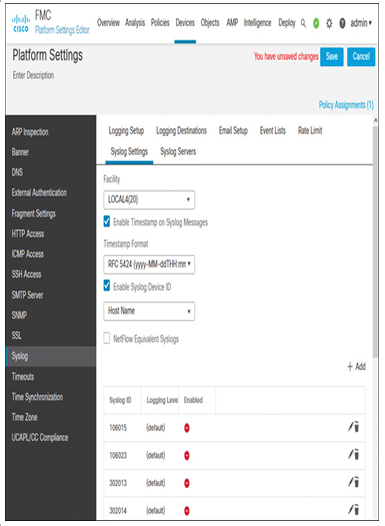
Figure 21-10 Enabling a Timestamp and a Device ID for Syslog Messages
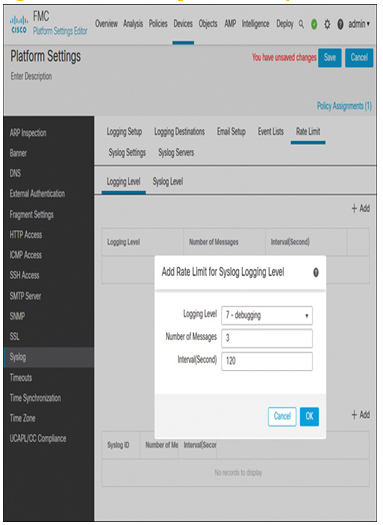
Figure 21-11 Rate Limiting of Debug-Level Syslog Messages
Step 7. After you finish enabling any optional settings, click Save to save the configurations to the platform settings policy.
Leave a Reply