Best Practices for Logging
Consider the following issues when configuring Secure Firewall to send alerts to a syslog server:
- If your syslog server uses TCP, enable the Allow User Traffic to Pass When TCP Syslog Server Is Down option. It enables the traffic flow to continue in case of any issues with the syslog server (shown later in Figure 21-9).
- To prevent a syslog server from crashing, you can enable rate limiting for certain types of syslog messages (shown later in Figure 21-11).
- Syslog over TCP can introduce overhead in a large deployment. In this scenario, syslog over UDP can improve performance.
- Do not associate a syslog server with an access control rule that has the potential to match a higher volume of traffic because it can send a lot of connection events for matching traffic.
Prerequisites
To learn and test the syslog configuration, you can utilize the same lab that you built in previous chapters. You can simply install the syslog service to your administrator computer. Figure 21-1 shows the lab topology used in the exercises of this chapter. Besides adding a syslog server, ensure the following items:
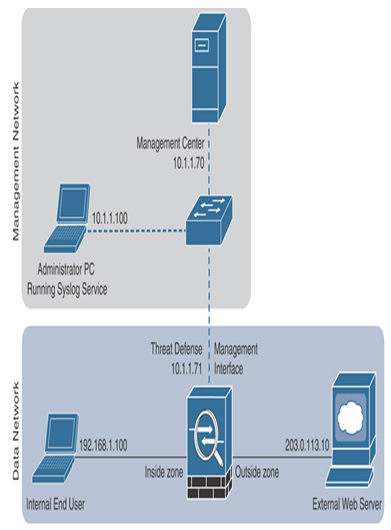
Figure 21-1 Lab Topology Used in This Chapter
- Make sure your management center and threat defense can reach the syslog server. While the management center uses its management interface for external communication, you can configure a threat defense device to use either its management interface or its named data interface to communicate with the syslog server (see Figure 21-2).
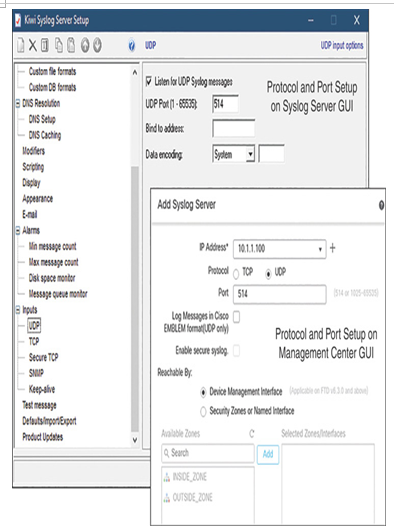
Figure 21-2 The Protocol and Port Number Need to Match on the Client and Server
- The syslog server should be configured to accept incoming syslog messages. The protocol and port number must match on both the client and server sides—Secure Firewall and the syslog server. Figure 21-2 shows that Secure Firewall is configured to send syslog messages over UDP port 514, and the syslog server also listens for syslog messages over UDP port 514. For the TCP protocol, syslog uses port 1470, by default.
- Add any necessary rules in the security policies that will trigger syslog alerts in your lab environment. For example, in the following sections, you will enable Secure Firewall to send syslog messages for file events and intrusion events. The file rule (shown in Figure 21-3) and the intrusion rule (shown in Figure 21-4) can do that job.
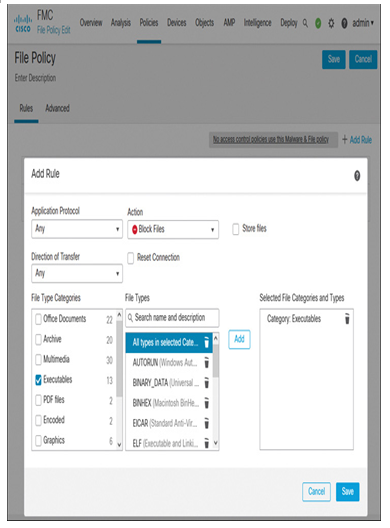
Figure 21-3 File Rule to Block Executable (MSEXE) Files
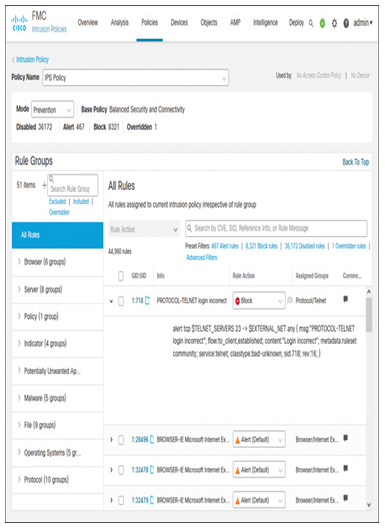
Figure 21-4 Intrusion Rule to Block Incorrect Login Attempts over Telnet
- Add an access control rule to match the traffic between the internal end user and external web server. Associate the intrusion policy and file policy with the access control rule, as shown in Figure 21-5.
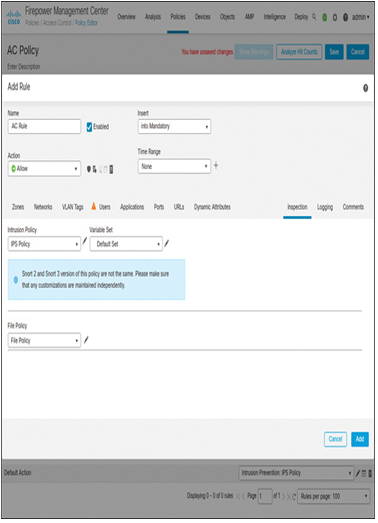
Figure 21-5 Association of Intrusion and File Policies with an Access Control Rule
Leave a Reply