Verification
When the remote access VPN policy is deployed on the threat defense, you can test the successful operation by using a browser in the remote host, as shown in the following steps:
Step 1. Log in to the remote host machine and open a browser.
Step 2. On the URL bar of the browser, enter the IP address of the threat defense’s outside interface. If the browser can connect to the threat defense successfully, it should prompt with a security warning because a browser does not trust a self-signed certificate, by default (see Figure 19-48).
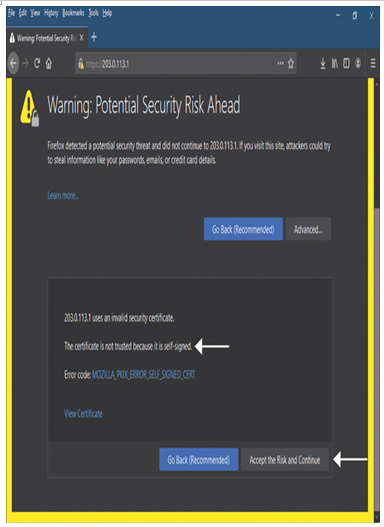
Figure 19-48 Security Warning on the Browser Due to Self-Signed Certificate
Tip
If the browser is unable to connect to the threat defense’s outside interface, check whether any existing settings on the threat defense, such as an access control policy or NAT policy, are blocking the connection. The “Verification” section under “Site-to-Site VPN Policy Deployment” describes the process.
Step 3. Because you used your Secure Firewall to generate this certificate earlier, you can accept the risk and continue this exercise in your lab environment.
Step 4. After you accept the risk, the login prompt appears (see Figure 19-49). Enter the username and password. The AAA server deployed in this lab environment validates this user credential. (The communication workflow between a remote user and AAA server is illustrated in Figure 19-35.)
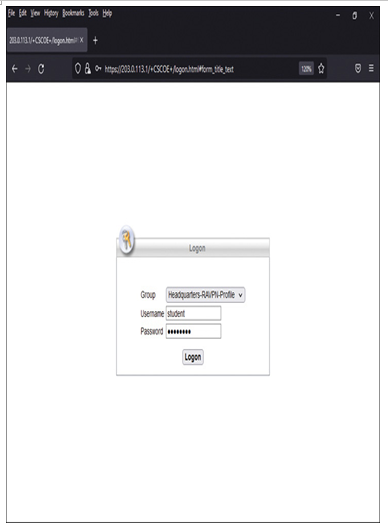
Figure 19-49 Connection Attempt to the Corporate Network Shows a Login Prompt
Step 5. Click the Logon button. The browser prompts you to download and install the AnyConnect Secure Mobility Client (see Figure 19-50). Download the software and install it on your computer.
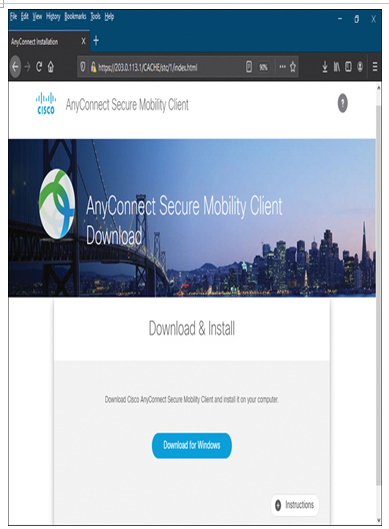
Figure 19-50 The Ability to Download and Install AnyClient Client Software Is Offered
Step 6. When the installation is complete, open the AnyConnect client software and perform the following tasks on the client:
- Enter the IP address of the threat defense outside interface on the client software.
- Click the Connect button. A login window appears (see Figure 19-51).
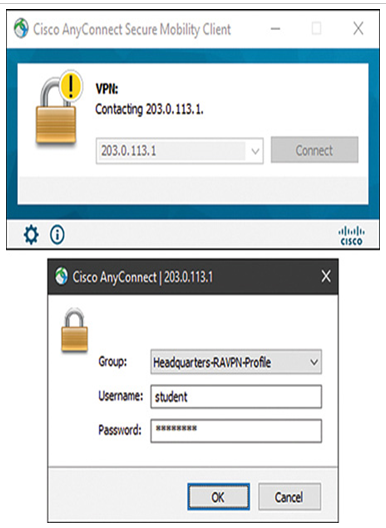
Figure 19-51 AnyConnect Client Login Prompt
- Enter the username and password (the same credential that you entered in Step 4).
- Click OK to log in. The AnyConnect client establishes a VPN session.
Step 7. You can verify the remote access connection status in various ways:
- As a remote user, you can open the AnyConnect client software to view the VPN connection status on the Message History tab (see Figure 19-52). You can also find the assigned IP address for this remote connection on the Statistics tab (see Figure 19-53).
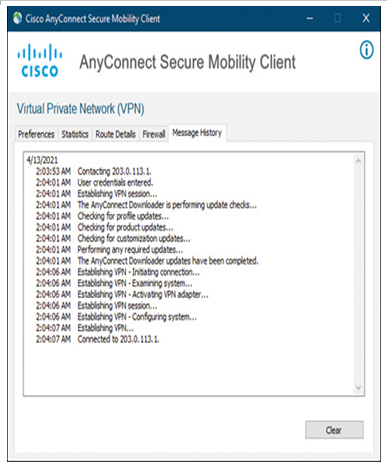
Figure 19-52 The AnyConnect Client Establishes a VPN Connection
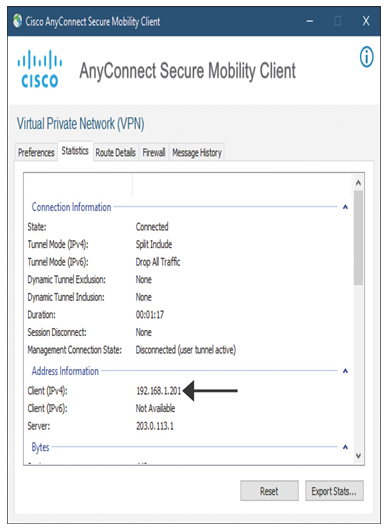
Figure 19-53 A Remote User Obtains an IP Address from the Threat Defense IPv4 Address Pool
- As a firewall administrator, you can log in to the management center and navigate to the Access Controlled User Statistics dashboard. The VPN tab displays various statistics about the active session in different widgets (see Figure 19-54).
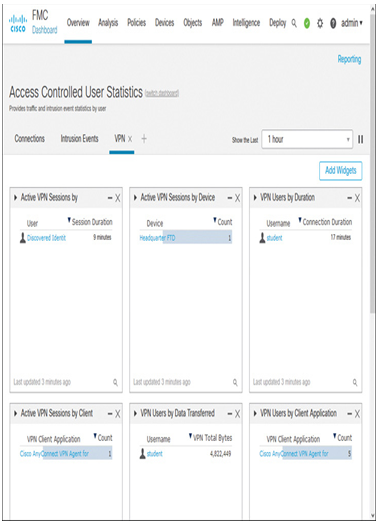
Figure 19-54 The Management Center Dashboard Shows VPN User Sessions
Example 19-7, Example 19-8, and Example 19-9 provide commands that you can run on the threat defense CLI to view the remote access VPN sessions. The command outputs in these examples represent a single user connection in this lab exercise.
Example 19-7 Viewing the VPN Session Database
>
show vpn-sessiondb detail
——————————————————————-
VPN Session Summary
——————————————————————-
Active : Cumulative : Peak Concur : Inactive
———————————————-
AnyConnect Client : 1 : 1 : 1 : 0
SSL/TLS/DTLS : 1 : 1 : 1 : 0
——————————————————————-
Total Active and Inactive : 1 Total Cumulative : 1
Device Total VPN Capacity : 75
Device Load : 1%
——————————————————————-
——————————————————————-
Tunnels Summary
——————————————————————-
Active : Cumulative : Peak Concurrent
———————————————-
AnyConnect-Parent : 1 : 1 : 1
SSL-Tunnel : 1 : 1 : 1
DTLS-Tunnel : 1 : 1 : 1
——————————————————————-
Totals : 3 : 3
——————————————————————-
>
Example 19-8 Viewing the AnyConnect Client Details
>
show vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : student Index : 10
Assigned IP : 192.168.1.201 Public IP : 203.0.113.100
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256
DTLS-Tunnel: (1)AES-GCM-256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)
SHA384
Bytes Tx : 15844 Bytes Rx : 104
Group Policy : DfltGrpPolicy
Tunnel Group : Headquarters-RAVPN-Profile
Login Time : 02:14:06 UTC Tue Apr 13 2021
Duration : 0h:01m:13s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 000000000000a0006074fe6e
Security Grp : none Tunnel Zone : 0
>
Example 19-9 Viewing the Detail Session
>
show vpn-sessiondb detail anyconnect
Session Type: AnyConnect Detailed
Username : student Index : 10
Assigned IP : 192.168.1.201 Public IP : 203.0.113.100
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel:
(1)AES-GCM-256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)
SHA384
Bytes Tx : 15844 Bytes Rx : 104
Pkts Tx : 12 Pkts Rx : 2
Pkts Tx Drop : 0 Pkts Rx Drop : 0
Group Policy : DfltGrpPolicy
Tunnel Group : Headquarters-RAVPN-Profile
Login Time : 02:14:06 UTC Tue Apr 13 2021
Duration : 0h:04m:06s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 000000000000a0006074fe6e
Security Grp : none Tunnel Zone : 0
AnyConnect-Parent Tunnels: 1
SSL-Tunnel Tunnels: 1
DTLS-Tunnel Tunnels: 1
AnyConnect-Parent:
Tunnel ID : 10.1
Public IP : 203.0.113.100
Encryption : none Hashing : none
TCP Src Port : 55911 TCP Dst Port : 443
Auth Mode : userPassword
Idle Time Out: 30 Minutes Idle TO Left : 25 Minutes
Client OS : win
Client OS Ver: 10.0.19042
Client Type : AnyConnect
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.10.00093
Bytes Tx : 7922 Bytes Rx : 0
Pkts Tx : 6 Pkts Rx : 0
Pkts Tx Drop : 0 Pkts Rx Drop : 0
SSL-Tunnel:
Tunnel ID : 10.2
Assigned IP : 192.168.1.201 Public IP : 203.0.113.100
Encryption : AES-GCM-256 Hashing : SHA384
Ciphersuite : ECDHE-RSA-AES256-GCM-SHA384
Encapsulation: TLSv1.2 TCP Src Port : 55920
TCP Dst Port : 443 Auth Mode : userPassword
Idle Time Out: 30 Minutes Idle TO Left : 26 Minutes
Client OS : Windows
Client Type : SSL VPN Client
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.10.00093
Bytes Tx : 7922 Bytes Rx : 104
Pkts Tx : 6 Pkts Rx : 2
Pkts Tx Drop : 0 Pkts Rx Drop : 0
DTLS-Tunnel:
Tunnel ID : 10.3
Assigned IP : 192.168.1.201 Public IP : 203.0.113.100
Encryption : AES-GCM-256 Hashing : SHA384
Ciphersuite : ECDHE-ECDSA-AES256-GCM-SHA384
Encapsulation: DTLSv1.2 UDP Src Port : 64814
UDP Dst Port : 443 Auth Mode : userPassword
Idle Time Out: 30 Minutes Idle TO Left : 26 Minutes
Client OS : Windows
Client Type : DTLS VPN Client
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.10.00093
Bytes Tx : 0 Bytes Rx : 0
Pkts Tx : 0 Pkts Rx : 0
Pkts Tx Drop : 0 Pkts Rx Drop : 0
>
Leave a Reply