Remote Access VPN Policy
Now is the time to put all the parts together. In the following steps, you use a wizard to configure a remote access VPN policy:
Step 1. Navigate to Devices > VPN > Remote Access.
Step 2. Click the Add button to create a new remote access VPN policy. The Remote Access VPN Policy Wizard opens. The policy wizard takes you through the necessary configuration steps, one by one.
Step 3. At first, configure the Policy Assignment, as shown in Figure 19-42.
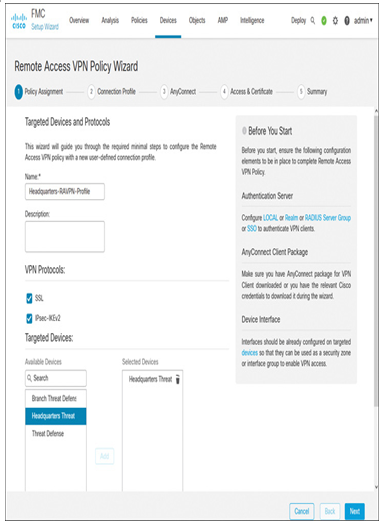
Figure 19-42 Remote Access VPN Policy Assignment Configuration
- Name this remote access VPN policy.
- Select the protocols for the VPN tunnel. You can select either SSL or IPsec IKEv2, or both.
- Add the threat defense where this policy will be deployed.
Step 4. Next, configure the Connection Profile.
- Choose an Authentication Method for the remotely connected users. This lab exercise uses AAA Only (see Figure 19-43).
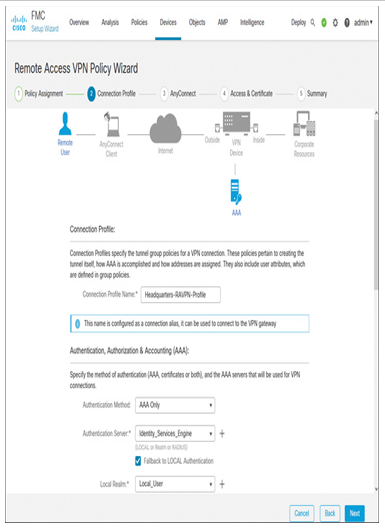
Figure 19-43 Connection Profile Page (Top Part)—Authentication Method Selection
- For authentication, authorization, and accounting services, select the RADIUS Server Group object that you created earlier. Optionally, select the Local Realm as a fallback to local authentication (described in the “Prerequisites” section; refer to Figure 19-34).
- Define a method to assign IP addresses to remote users. As shown in Figure 19-44, the threat defense will assign addresses from the RAVPN_IP_Pool when remote users connect to the organization’s network via the remote access VPN tunnel. You created this object earlier (refer to Figure 19-41).
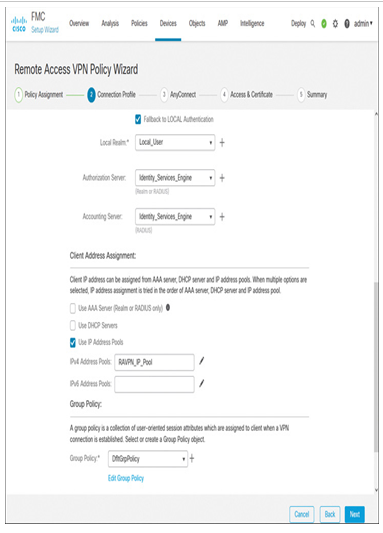
Figure 19-44 Connection Profile Page (Bottom Part)—Client Address and Group Policy Assignment
- For Group Policy, you can create and select a new policy. For this chapter, select DfltGrpPolicy, which is the default group policy.
Step 5. In the next section, select one or more AnyConnect client images that you uploaded to the management center earlier (see Figure 19-45).
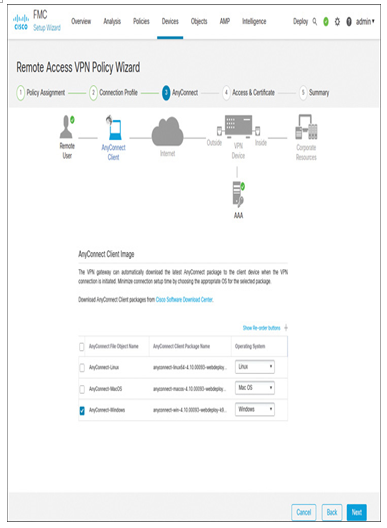
Figure 19-45 AnyConnect Client Image Selection in a Policy
Step 6. Finally, in the Access & Certificate section, choose the desired options from the drop-down, as displayed in Figure 19-46.
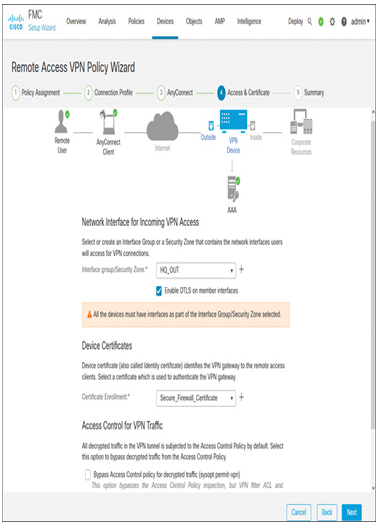
Figure 19-46 Configurations for Incoming VPN Access
- Select the security zone, HQ_OUT, which is associated with the outside interface of the threat defense. In the remote access VPN lab topology, the remote users use the outside interface to connect to the organization network.
- Select Secure_Firewall_Certificate, which you installed on the threat defense earlier. This certificate is used to authenticate the VPN headend.
Step 7. The Summary section shows all the options you configured so far (see Figure 19-47). Click Finish if everything looks good.
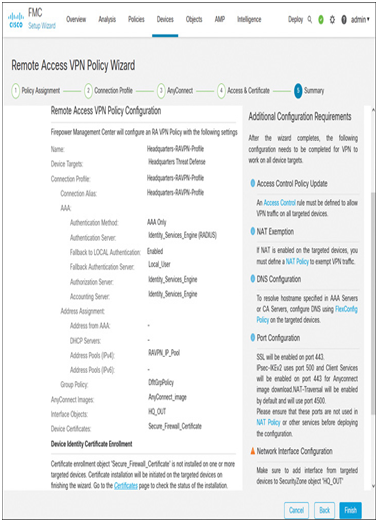
Figure 19-47 Summary of Remote Access VPN Policy Configurations
Step 8. Navigate to the Deploy > Deployment page to deploy the remote access VPN policy to your threat defense.
Leave a Reply