Certificate Enrollment
You can use the Cert Enrollment object to enter information about the certification authority (CA) server in your public key infrastructure (PKI). This information is necessary to create a certificate signing request (CSR) and to obtain an identity certificate. Secure Firewall offers four ways to select an enrollment type:
- PKCS12 File: Import a Public Key Cryptography Standard (PKCS) file into Secure Firewall. A PKCS12 file is a single encrypted file that can contain information about the server certificate, any intermediate certificates, and the private key.
- SCEP: Use the Simple Certificate Enrollment Protocol (SCEP) to establish a direct connection between a threat defense and a CA server, and allow the threat defense to obtain an identity certificate directly from the CA.
- Manual: Copy the certificate information that you obtain from a CA server and paste it manually on Secure Firewall.
- Self-signed: Allow the threat defense to act as a CA server using its self-signed root certificate.
Because describing the configuration and deployment of an external CA server is beyond the scope of this book, this chapter uses the self-signed certificate to demonstrate the configuration of remote access VPN services on a threat defense. Use the following steps to add a self-signed certificate to a threat defense:
Step 1. Go to Objects > Object Management.
Step 2. Select PKI > Cert Enrollment on the left panel.
Step 3. Click the Add Cert Enrollment button. It opens the Add Cert Enrollment configuration window.
Step 4. On the CA Information tab, select Self Signed Certificate from the Enrollment Type drop-down.
Step 5. When you select the self-signed certificate enrollment type, you also need to provide a Common Name (CN). This field is located on the Certificate Parameters tab, as shown in Figure 19-38.
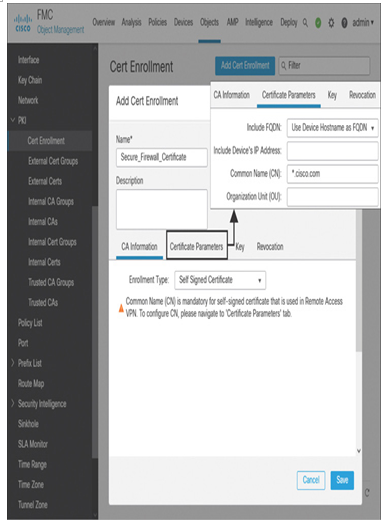
Figure 19-38 Creating a Certificate Enrollment Object
Step 6. Click the Save button to save the Cert Enrollment object.
Step 7. After adding the object, go to Devices > Certificates to add the certificate to your Secure Firewall (see Figure 19-39). After the certificate is added successfully, you can view the identity certificate by clicking the ID button (see Figure 19-40).
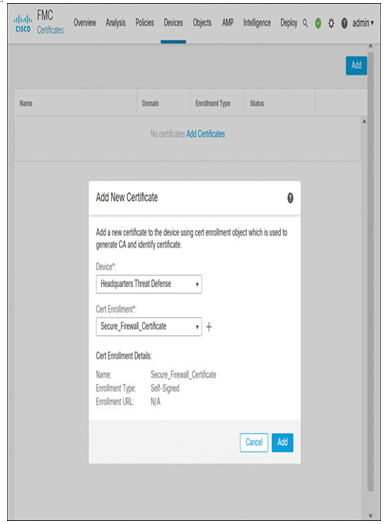
Figure 19-39 Adding a Certificate to the Threat Defense
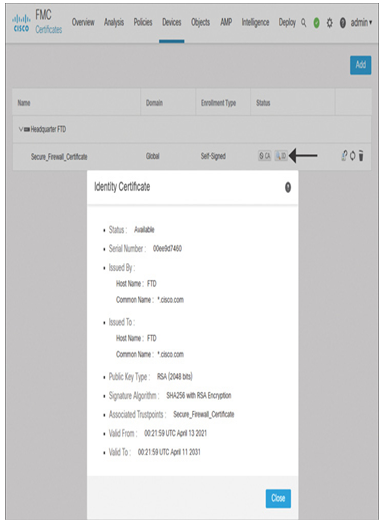
Figure 19-40 Viewing the Detail of an Identity Certificate
Network and IP Address Pool
To represent the IP addresses of both local-area network users and the remote access users, you can add the following types of objects after navigating to Objects > Object Management:
- Network: A network object can be added to represent the local-area network at headquarters. If you created network objects for the site-to-site VPN lab exercises in the previous section, you could reuse them here.
- Address pools: An address pool object contains the pre-allocated IP addresses for remote users. An IP address from this pool is assigned to a remote user when the user connects to the organization’s internal network over the Internet using the remote-access VPN tunnel.
Figure 19-41 shows the addition of two objects. The top part of the figure shows the HQ_LAN network object, which defines the local-area network of the headquarters. Likewise, the bottom part of the figure shows the RAVPN_IP_Pool object, which defines an IPv4 address pool for remote users.
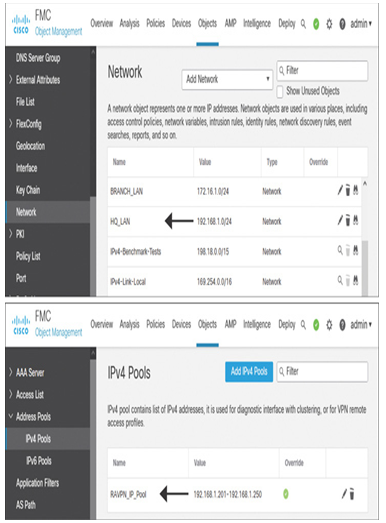
Figure 19-41 Objects to Represent the LAN and Remote Users’ Network Addresses
Leave a Reply