Configuration
Implementation of remote access VPN services on Secure Firewall is not a straightforward process. Before you begin the core part of the remote access VPN configuration, you need to define several components in various types of objects. When the necessary objects are configured, you invoke them into the Remote Access VPN Policy Wizard to configure the remote access VPN. The following sections walk you through all the necessary configurations.
AnyConnect File
The AnyConnect Secure Mobility Client software empowers a remote user to connect to the internal network of an organization from any geographic location. It supports both SSL and IPsec IKEv2 protocols to establish a secure connection. The AnyConnect client supports various operating systems, such as Windows, Mac OS, and Linux. You can download the software package for your desired operating system from the Cisco Software Download Center. After you download the files, you need to upload them to the management center. Follow these steps to upload:
Step 1. Navigate to Objects > Object Management on your management center.
Step 2. Select VPN > AnyConnect File from the left panel.
Step 3. Click the Add AnyConnect File button to upload the client software package files.
Figure 19-36 shows the upload of three different AnyConnect client software package files for Linux, Mac OS, and Windows operating systems.
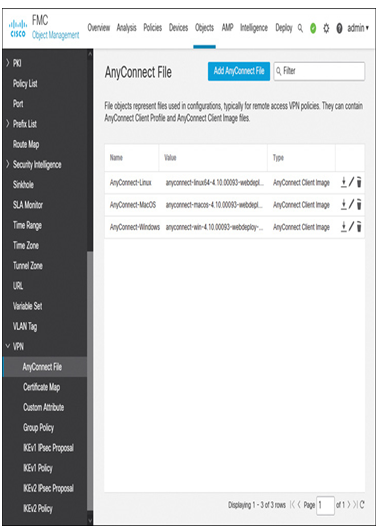
Figure 19-36 Uploading the AnyConnect Files to the Management Center
RADIUS Server Group
Using the AAA Server > RADIUS Server Group object, you can add a single server or a group of servers that can be used to authenticate many remote access VPN users. The lab exercises in this chapter use an ISE server for AAA services. (Optionally, a local user is also added as a fallback, as shown in Figure 19-34.)
Figure 19-37 shows the creation of a RADIUS Server Group object, named Identity_Services_Engine, to describe the connection parameters of an authentication server. In the Key and Confirm Key fields, enter the shared secret key that is also used in the ISE server. This key is used to encrypt data between the threat defense and the ISE server.
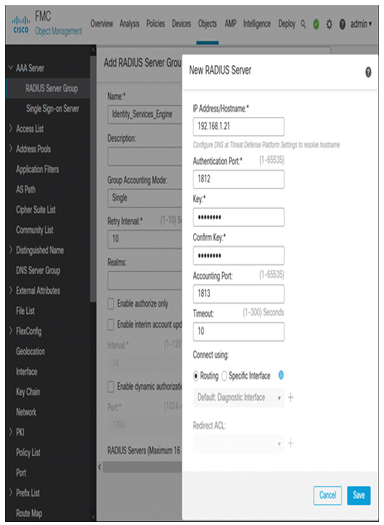
Figure 19-37 Object to Define the User Authentication Server
Leave a Reply