Prerequisites
Before you begin configuring the remote access VPN services, fulfill the following prerequisites:
- Register a threat defense, which will provide remote access VPN services in the headquarters, with a management center. Configure the ingress and egress interfaces of the threat defense in routed mode with the necessary IP addresses. If the interfaces of the Headquarters Threat Defense are configured as a part of the site-to-site VPN lab exercises (as shown in Figure 19-19), you can reuse them now. Note that, unlike the site-to-site VPN lab exercises, the remote access VPN lab requires only one threat defense, which will act as a headend (see Figure 19-32).
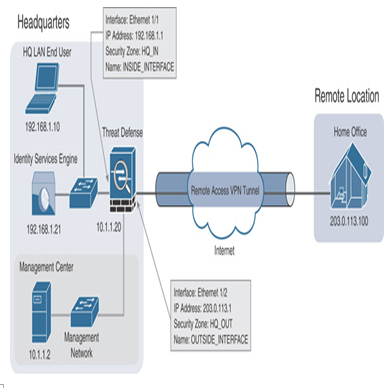
Figure 19-32 Lab Topology to Implement the Remote Access VPN Services
- When registering your management center with Cisco Smart Software Licensing, you must allow the export-controlled functionality, as shown in Figure 19-16. It allows you to enable strong cryptographic features on your Cisco Secure Firewall. If the export-controlled functionality is not allowed, you can use only the Data Encryption Standard (DES) algorithm to encrypt data. Likewise, if you run Secure Firewall in Evaluation Mode, DES is the only encryption algorithm you can implement.
- Acquire and enable one of the AnyConnect features licenses for your threat defense. There are three tiers of AnyConnect licenses: AnyConnect Plus, AnyConnect Apex, and AnyConnect VPN Only. The AnyConnect Plus license offers the basic remote-access VPN services, whereas the AnyConnect Apex license allows you to enable many advanced features in addition to the basic features provided by the AnyConnect Plus license.
If you choose between AnyConnect Plus and AnyConnect Apex license tiers, you must consider the total number of unique users who may be using remote access VPN services at any time. In contrast, the AnyConnect VPN Only license allows any number of unique users to connect to a threat defense. However, in this case, the total number of simultaneous connections processed by a specific threat defense at any time is limited by the AnyConnect VPN Only license.
Tip
The performance of remote access VPN services depends on the threat defense model and the AnyConnect license you choose. In other words, when designing a remote access VPN service for your organization, you must carefully estimate the maximum bandwidth requirements of your organization as well as the maximum number of simultaneous remote user sessions that will be processed by a headend threat defense. Therefore, read the Secure Firewall datasheet and orderability guide to select an appropriate device model and AnyConnect license tier.
- Enable the AnyConnect licenses on the threat defense using the management center. To enable the license, go to Devices > Device Management, and edit the device settings of the threat defense where you want to configure the remote access VPN. On the Device tab, as shown in Figure 19-33, you can enable your desired license types.
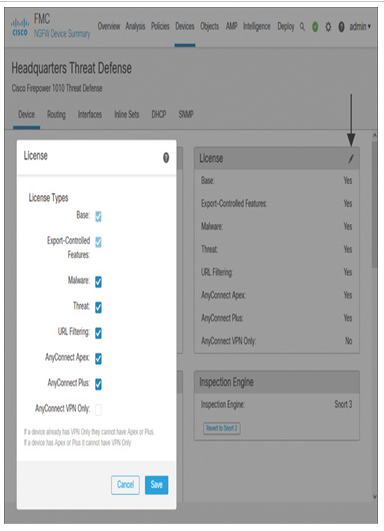
Figure 19-33 Enabling the AnyConnect License on Secure Firewall
- Secure Firewall Version 7.x or higher supports local user authentication. You can use its local user database to authenticate users for remote access VPN connections. Although setting up a few local users may be a faster way to demonstrate the remote-access VPN operations, a large organization requires a dedicated AAA server to manage thousands of users. In a real-world scenario, you enable local authentication as a fallback mechanism. You can add a new realm for local users by going to System > Integration > Realms (see Figure 19-34).
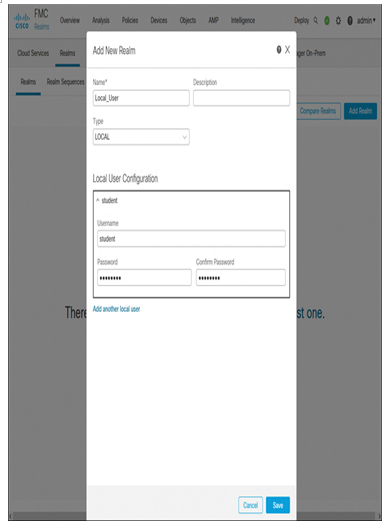
Figure 19-34 Local User Configuration on the Management Center
If your Secure Firewall runs an earlier software version, a separate AAA server is necessary to authenticate the remote access VPN users. The lab exercises in this chapter use the Cisco Identity Service Engine (ISE) as the primary AAA server and the local user database as a fallback. For your lab testing, you can choose to use both or any one of the authentication methods. Describing an ISE server is beyond the scope of this book, but you can find details in the ISE configuration guide, published at cisco.com.
Figure 19-35 shows the workflow for validating a remote user credential by an AAA server through a VPN gateway.
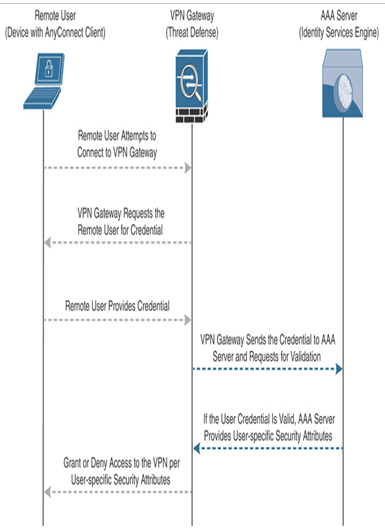
Figure 19-35 Communication Between a Remote User, VPN Gateway, and AAA Server
Leave a Reply