Verification
This section assumes that end users between the headquarters and branch sites can communicate successfully over the IPsec tunnel. To verify the operations of an IPsec tunnel, you can use one of the hosts in the headquarters to connect to a host in the branch office. Sending a simple ICMP ping request, as shown in Example 19-1, would establish a connection over the IPsec VPN tunnel.
Example 19-1 Successful Ping Test Through an IPsec VPN Tunnel
user@Headquarters:~$
ping 172.16.1.10
PING 172.16.1.10 (172.16.1.10) 56(84) bytes of data.
64 bytes from 172.16.1.10: icmp_seq=2 ttl=64 time=2.34 ms
64 bytes from 172.16.1.10: icmp_seq=3 ttl=64 time=2.15 ms
64 bytes from 172.16.1.10: icmp_seq=4 ttl=64 time=2.30 ms
64 bytes from 172.16.1.10: icmp_seq=5 ttl=64 time=2.08 ms
^C
— 172.16.1.10 ping statistics —
5 packets transmitted, 4 received, 20% packet loss, time 4023ms
rtt min/avg/max/mdev = 2.087/2.221/2.342/0.110 ms
user@Headquarters:~$
When the policy deployment is successful, you can use the CLI of the threat defense to review the configurations. As you know, you can run the show running-config command to view the running configuration. Adding the crypto parameter with the command displays the VPN configurations only, as shown in Example 19-2.
Example 19-2 IPsec Site-to-Site VPN Configurations on a Threat Defense
>
show running-config crypto
crypto ipsec ikev2 ipsec-proposal CSM_IP_1
protocol esp encryption aes-gcm-256 aes-gcm-192 aes-gcm
protocol esp integrity null
crypto ipsec security-association pmtu-aging infinite
crypto map CSM_Outside_Interface_map 1 match address CSM_IPSEC_ACL_1
crypto map CSM_Outside_Interface_map 1 set peer 203.0.113.2
crypto map CSM_Outside_Interface_map 1 set ikev2 ipsec-proposal CSM_IP_1
crypto map CSM_Outside_Interface_map 1 set reverse-route
crypto map CSM_Outside_Interface_map interface OUTSIDE_INTERFACE
crypto ca trustpool policy
crypto ikev2 policy 1
encryption aes-256
integrity sha512
group 21
prf sha512
lifetime seconds 86400
crypto ikev2 enable OUTSIDE_INTERFACE
crypto ikev1 am-disable
>
Figure 19-31 shows the exchange of two pairs of packets for IKEv2 negotiation followed by the four pairs of packets for the ping test. The packets for ICMP requests and responses are encapsulated by the ESP header.
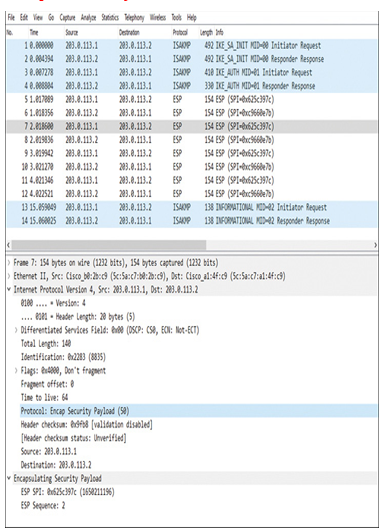
Figure 19-31 ICMP Packets Through an IPsec VPN Tunnel
To find detailed statistics about the VPN sessions in a threat defense, run the show vpn-sessiondb detail command. To view details of IKEv2 and IPsec attributes used in the VPN sessions, add the l2l (alpha lowercase L, numeric 2, and a second alpha lowercase L) parameters with the command, as shown in Example 19-3.
Example 19-3 Displaying VPN Session Details
! To display VPN session statistics:
>
show vpn-sessiondb detail
——————————————————————-
VPN Session Summary
——————————————————————-
Active : Cumulative : Peak Concur : Inactive
———————————————-
Site-to-Site VPN : 1 : 1 : 1
IKEv2 IPsec : 1 : 1 : 1
——————————————————————-
Total Active and Inactive: 1 Total Cumulative : 1
Device Total VPN Capacity: 75
Device Load : 1%
——————————————————————-
——————————————————————-
Tunnels Summary
——————————————————————-
Active : Cumulative : Peak Concurrent
———————————————-
IKEv2 : 1 : 1 : 1
IPsec : 1 : 1 : 1
——————————————————————-
Totals : 2 : 2
——————————————————————-
>
! To display LAN-to-LAN VPN session information:
>
show vpn-sessiondb detail l2l
Session Type: LAN-to-LAN Detailed
Connection : 203.0.113.2
Index : 1 IP Addr : 203.0.113.2
Protocol : IKEv2 IPsec
Encryption : IKEv2: (1)AES256 IPsec: (1)AES-GCM-256
Hashing : IKEv2: (1)SHA512 IPsec: (1)none
Bytes Tx : 3780 Bytes Rx : 3780
Login Time : 22:02:36 UTC Sat Mar 27 2021
Duration : 0h:04m:11s
Tunnel Zone : 0
IKEv2 Tunnels: 1
IPsec Tunnels: 1
IKEv2:
Tunnel ID : 1.1
UDP Src Port : 500 UDP Dst Port : 500
Rem Auth Mode: preSharedKeys
Loc Auth Mode: preSharedKeys
Encryption : AES256 Hashing : SHA512
Rekey Int (T): 86400 Seconds Rekey Left(T): 86148 Seconds
PRF : SHA512 D/H Group : 21
Filter Name :
IPsec:
Tunnel ID : 1.2
Local Addr : 192.168.1.0/255.255.255.0/0/0
Remote Addr : 172.16.1.0/255.255.255.0/0/0
Encryption : AES-GCM-256 Hashing : none
Encapsulation: Tunnel
Rekey Int (T): 28800 Seconds Rekey Left(T): 28548 Seconds
Rekey Int (D): 4608000 K-Bytes Rekey Left(D): 4607997 K-Bytes
Idle Time Out: 30 Minutes Idle TO Left : 26 Minutes
Bytes Tx : 3780 Bytes Rx : 3780
Pkts Tx : 45 Pkts Rx : 45
>
After an IPsec tunnel is established successfully, you can view the detailed statistics of the security associations from the CLI. Run the show crypto ikev2 sa detail command (see Example 19-4) for IKEv2 security associations and the show crypto ipsec sa detail command for IPsec security associations (see Example 19-5).
Example 19-4 IKEv2 Security Association Detail
>
show crypto ikev2 sa detail
IKEv2 SAs:
Session-id:1,
Status:UP-ACTIVE
, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
19066247 203.0.113.1/500 203.0.113.2/500 READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA512, DH Grp:21, Auth sign: PSK, Auth
verify: PSK
Life/Active Time: 86400/216 sec
Session-id: 1
Status Description: Negotiation done
Local spi: 1BBE8980EB3784BB Remote spi: 91154FB2E3E310F0
Local id: 203.0.113.1
Remote id: 203.0.113.2
Local req mess id: 18 Remote req mess id: 0
Local next mess id: 18 Remote next mess id: 0
Local req queued: 18 Remote req queued: 0
Local window: 1 Remote window: 1
DPD configured for 10 seconds, retry 2
NAT-T is not detected
IKEv2 Fragmentation Configured MTU: 576 bytes, Overhead: 28 bytes, Effective
MTU: 548 bytes
Parent SA Extended Status:
Delete in progress: FALSE
Marked for delete: FALSE
Child sa: local selector 192.168.1.0/0 – 192.168.1.255/65535
remote selector 172.16.1.0/0 – 172.16.1.255/65535
ESP spi in/out: 0xe62a8d7b/0xbc4877fd
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-GCM, keysize: 256, esp_hmac: N/A
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
>
Example 19-5 IPsec Security Association Detail
>
show crypto ipsec sa detail
interface: OUTSIDE_INTERFACE
Crypto map tag: CSM_Outside_Interface_map, seq num: 1, local addr: 203.0.113.1
access-list CSM_IPSEC_ACL_1 extended permit ip 192.168.1.0 255.255.2S55.0
172.16.1.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
current_peer: 203.0.113.2
#pkts encaps: 45, #pkts encrypt: 45, #pkts digest: 45
#pkts decaps: 45, #pkts decrypt: 45, #pkts verify: 45
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 45, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#pkts no sa (send): 0, #pkts invalid sa (rcv): 0
#pkts encaps failed (send): 0, #pkts decaps failed (rcv): 0
#pkts invalid prot (rcv): 0, #pkts verify failed: 0
#pkts invalid identity (rcv): 0, #pkts invalid len (rcv): 1396264912
#pkts invalid pad (rcv): 0,
#pkts invalid ip version (send): 0, #pkts invalid ip version (rcv): 0
#pkts invalid len (send): 0, #pkts invalid len (rcv): 0
#pkts invalid ctx (send): 0, #pkts invalid ctx (rcv): 0
#pkts invalid ifc (send): 0, #pkts invalid ifc (rcv): 0
#pkts failed (send): 0, #pkts failed (rcv): 0
#pkts replay rollover (send): 0, #pkts replay rollover (rcv): 0
#pkts replay failed (rcv): 0
#pkts min mtu frag failed (send): 0, #pkts bad frag offset (rcv): 0
#pkts internal err (send): 0, #pkts internal err (rcv): 0
local crypto endpt.: 203.0.113.1/500, remote crypto endpt.: 203.0.113.2/500
path mtu 1500, ipsec overhead 55(36), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: BC4877FD
current inbound spi : E62A8D7B
inbound esp sas:
spi: 0xE62A8D7B (3861548411)
SA State: active
transform: esp-aes-gcm-256 esp-null-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 1, crypto-map: CSM_Outside_Interface_map
sa timing: remaining key lifetime (kB/sec): (4101116/28719)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00003FFF 0xFFFFFFFF
outbound esp sas:
spi: 0xBC4877FD (3158865917)
SA State: active
transform: esp-aes-gcm-256 esp-null-hmac no compression
in use settings ={L2L, Tunnel, IKEv2, }
slot: 0, conn_id: 1, crypto-map: CSM_Outside_Interface_map
sa timing: remaining key lifetime (kB/sec): (4055036/28719)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
>
If the NAT exemption is enabled on a VPN gateway to exclude the translation of internal IP addresses, you can confirm the deployment of an identity NAT rule by looking into the output of the show running-config nat command (see Example 19-6). Additionally, the show xlate detail command confirms the exemption from address translation performed by an identity rule.
Example 19-6 Implementation of a NAT Exemption
>
show running-config nat
nat (INSIDE_INTERFACE,OUTSIDE_INTERFACE) source static
HQ_LAN HQ_LAN
destination
static
Branch_LAN Branch_LAN
no-proxy-arp route-lookup
!
object network HQ_LAN
nat (INSIDE_INTERFACE,OUTSIDE_INTERFACE) dynamic interface
>
>
show xlate detail
2 in use, 2 most used
Flags: D – DNS, e – extended,
I – identity
, i – dynamic, r – portmap,
s – static, T – twice, N – net-to-net
NAT from INSIDE_INTERFACE:192.168.1.0/24 to OUTSIDE_INTERFACE:192.168.1.0/24
flags s
I
T idle 0:00:00 timeout 0:00:00 refcnt 0 xlate id 0x2b8047a7a3c0
NAT from OUTSIDE_INTERFACE:172.16.1.0/24 to INSIDE_INTERFACE:172.16.1.0/24
flags s
I
T idle 0:00:00 timeout 0:00:00 refcnt 0 xlate id 0x2b8047a7a1c0
>
Leave a Reply