Access Control Policy
If end-user traffic is blocked by the access control policy, you can allow the traffic in two ways:
- Option 1: You can add access control rules explicitly to match and allow traffic between both LANs (headquarters and branch), as shown in Figure 19-25. In this case, if the access control policy is set to block all traffic by default, the end-user traffic between both sites is still allowed by the access control rules. If you assign an intrusion policy for each access control rule, the matching traffic is also subject to deep packet intrusion inspection.
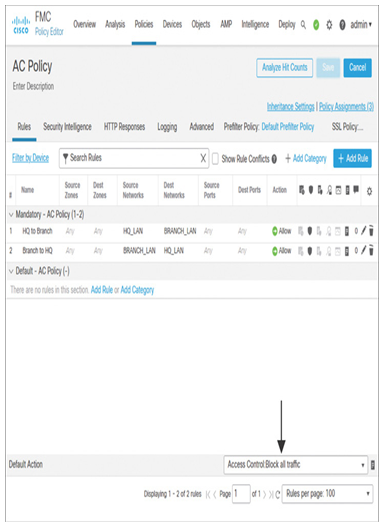
Figure 19-25 Allowing End-User Traffic Specifically Between Two Sites
- Option 2: If no access control rule is added to match the LAN traffic, the default action of the access control policy can permit the traffic. Figure 19-26 shows the selection of an intrusion policy as the default action. Allowing traffic without any sort of inspection would introduce security risks.
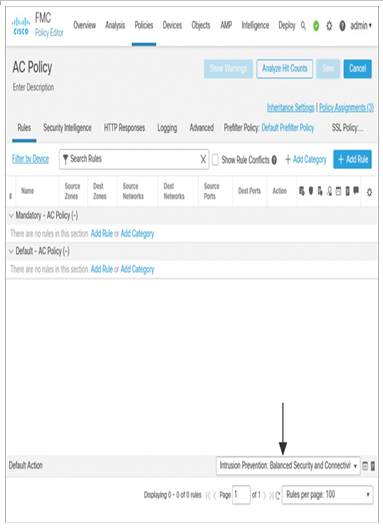
Figure 19-26 Allowing All Traffic After Intrusion Inspection
NAT Policy
Network Address Translation is discussed in the aptly titled Chapter 17, “Network Address Translation (NAT).” NAT is used to translate private IP addresses into routable, public addresses. In a real-world scenario, if an interface of the threat defense is configured to perform address translation as well as to establish a site-to-site VPN tunnel, you need to exempt the internal traffic from being translated by adding an identity NAT rule. This is known as a NAT exemption. In an identity NAT rule, the original source address and the translated source address are usually kept the same. The same is true for the destination address: the original destination address and the translated destination remain the same.
For example, Figure 19-27 shows a dynamic NAT rule that translates all the internal IP addresses into the outside interface address. Because the outside interface is also configured to establish a site-to-site VPN tunnel, an identity NAT rule is configured to exclude the internal traffic from being translated, as shown in Figure 19-28.
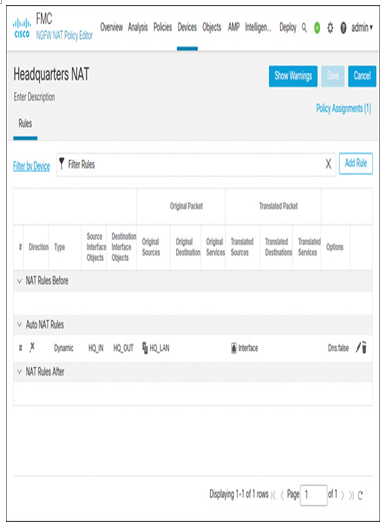
Figure 19-27 NAT Rule to Translate Internal Addresses to Destination Interface IP Addresses
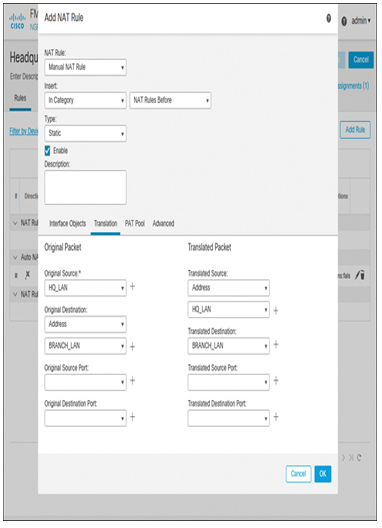
Figure 19-28 Identity NAT Rule Configuration
Figure 19-29 and Figure 19-30 show two different identity NAT rules in two separate NAT policies that can be deployed in headquarters and branch threat defense devices.
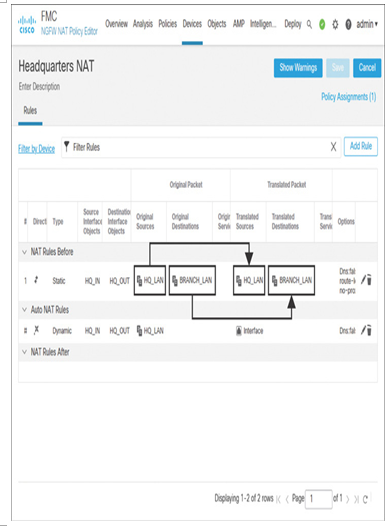
Figure 19-29 NAT Policy for Headquarters to Perform a NAT Exemption
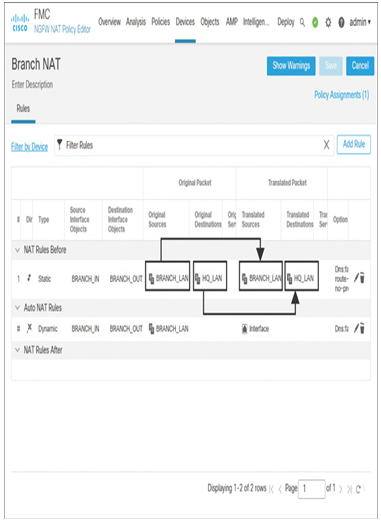
Figure 19-30 NAT Policy for a Branch Site to Perform a NAT Exemption
Leave a Reply