Traffic Decryption Essentials
Secrecy and privacy are of vital importance for communication. Prior to the electronic communication era, a person was appointed as a messenger. Sometimes, a pigeon was used for its homing instinct. However, neither a person nor a pigeon was able to ensure the confidentiality of a message. The longer the distance they had to travel, the more vulnerable the messengers and their messages were. Furthermore, to decode any messages, the recipient had to know the sender’s secret key and encoding technique. Sending secrets along with the messages was not a wise decision. Thus, cryptanalysis began to evolve hundreds of years ago. Cryptanalysis is a domain in which the methods of decrypting any encrypted messages are studied. Al-Kindi (Born: 801 AD, Iraq) is known as the father of cryptanalysis.
Figure 18-1 shows the design of a simple algorithm to encipher any plaintexts. Here, each letter in the English alphabet is shifted by 3. It means, in ciphertext, the letter A represents the letter D (A+3).
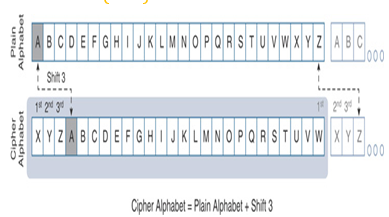
Figure 18-1 Designing a Simple Cipher Code
Figure 18-2 displays two different approaches to encipher the word CRYPTOGRAPHY. It uses the cipher alphabet shown in Figure 18-1. Modern cryptographic algorithms are so complicated that they require computers with higher computational power for encryption and decryption operations (see Figure 18-3). The new generation of Cisco Secure Firewall comes with dedicated processors for cryptographic operations.
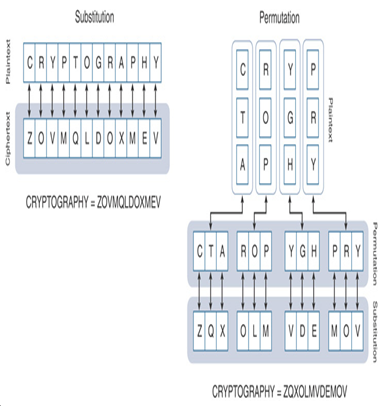
Figure 18-2 Concept of Encryption and Decryption Using a Simple Cipher
Figure 18-3 High-Level Workflow of Cryptographic Operations
Overview of SSL and TLS Protocols
The Secure Socket Layer (SSL) protocol was originally developed by Taher Elgamal (Born: 1955 AD, Egypt) when he was working at Netscape Communications. Since its first draft, the SSL protocol has gone through many revisions and improvements to ensure protection against any new vulnerabilities. When SSL protocol version 3 was revised to address a vulnerability with a man-in-the-middle attack (known as the POODLE attack), the new edition of the protocol was renamed the Transport Layer Security (TLS).
Although the SSL protocol is deprecated, many people still use the pioneering term SSL to refer to its successor, the TLS protocol. For example, on the Secure Firewall GUI, you add an “SSL Rule” in an “SSL Policy” to decrypt traffic that can be encrypted by either SSL or TLS protocol. Here, both protocols—SSL and TLS—are used interchangeably.
The TLS protocol has also gone through several revisions since its first release. TLS 1.2 has been a widely deployed cryptographic protocol. Ten years after its release, the Internet Engineering Task Force (IETF) defined its successor—TLS 1.3—in RFC 8446 in 2018. Figure 18-4 shows the evolution of SSL and TLS protocol versions, their release dates, and references to the standardized documents.
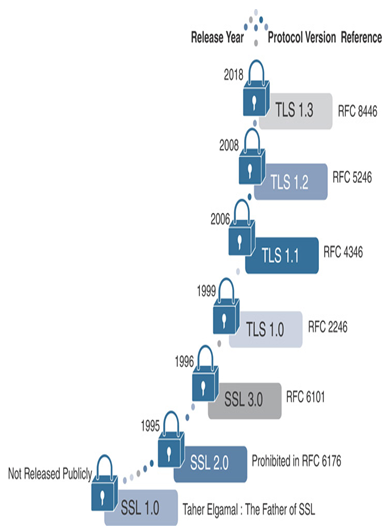
Figure 18-4 Evolution of SSL and TLS Protocols
Secure Firewall uses the protocol handshake to determine the exact protocol version used in an encrypted session. After the TCP three-way handshake (SYN, SYN-ACK, ACK) is complete, the TLS handshake begins with a Hello message from the client, followed by another Hello message from the server, as a response. During the TLS handshake, the client and server negotiate the security parameters they can support and exchange encryption keys to establish a secure TLS connection. Depending on the TLS version, the client/server handshake may differ (see Figure 18-5 and Figure 18-6). TLS 1.2 requires two round trips to complete its handshake. However, TLS 1.3 allows a client and server to complete the handshake in just in one round trip. This reduces latency introduced by the encryption process, as illustrated in Figure 18-7. TLS 1.3 also deprecates obsolete ciphers and algorithms that are known for potential security vulnerabilities, such as RC4, DES, and MD5. The list of supported cipher suites in TLS 1.3 is much shorter than the list for TLS 1.2.
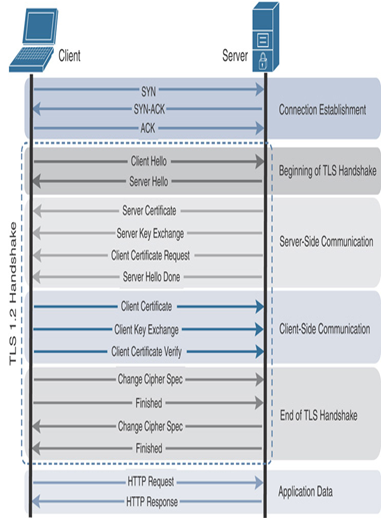
Figure 18-5 Detail View of TLS 1.2 Handshakes
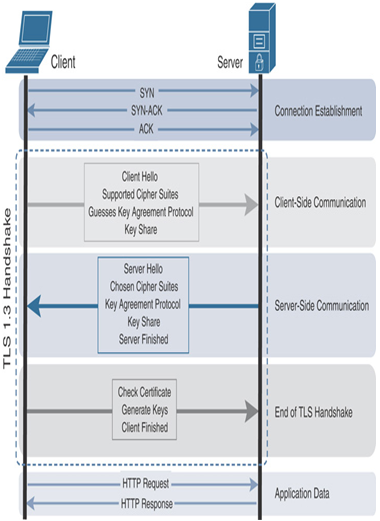
Figure 18-6 Detail View of TLS 1.3 Handshakes
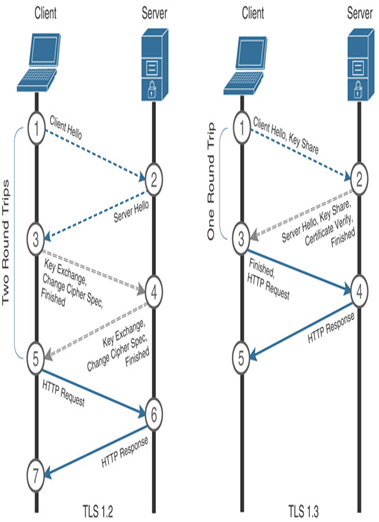
Figure 18-7 Round Trips Comparison by TLS 1.2 and TLS 1.3
Leave a Reply