Decryption Techniques on Secure Firewall
The full suite of access control rule capabilities can be performed only on nonencrypted traffic. To decrypt, inspect, and block encrypted traffic, you need to configure an SSL policy and select the SSL policy from within your access control policy. When an SSL policy is associated with an access control policy, Secure Firewall uses that SSL policy to act on any encrypted traffic before the traffic can be evaluated by the access control policy rules. Depending on the direction of traffic, Secure Firewall offers two techniques to decrypt traffic (see Figure 18-8): decryption by resigning (for outgoing traffic) and decryption using known key (for incoming traffic).
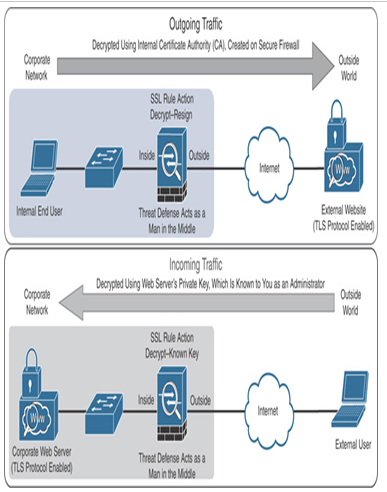
Figure 18-8 Decryption Techniques Are Influenced by Traffic Direction
- Decryption by resigning (for outgoing traffic): This technique is used to decrypt outgoing traffic from an internal end user—when the user attempts to connect to an external web server located outside your organization. It enables Secure Firewall to intercept outgoing encrypted traffic much like a proxy or man-in-the-middle. It completes the SSL handshake on behalf of the client that initiated the connection and is then able to decrypt the traffic for evaluation by the access control policy and perform further inspection if further inspection is configured in the rule that allows the traffic. If the traffic passes inspection, it re-encrypts the traffic and sends it off to its destination.
Using this method, a threat defense builds a TLS tunnel with the internal end user using a preconfigured trusted certificate issued by an internal certificate authority (CA). On the other side, a separate TLS tunnel is established simultaneously between the threat defense and the destination website. From the end user’s perspective, the connection is transparent and the user is not aware that an intermediate device, Secure Firewall, between the user and the destination has intervened.
- Decryption by known key (for incoming traffic): This technique is used to decrypt incoming traffic—in other words, traffic from external sources destined for servers that belong to you located behind Secure Firewall. Because you or your organization owns the server, you can gain access to the server’s private key, if needed. In other words, the server’s private key is known to you.
To implement this method, you upload the server’s private key to the management center. After the SSL policy deployment, the threat defense can use this private key to decrypt and re-encrypt any incoming traffic. This way, you can protect your internal web server from an external attack.
Note
Secure Firewall software version 7.1 introduces the Encrypted Visibility Engine, which can passively identify client software information and threats within encrypted traffic. It uses the machine learning technology based on TLS fingerprinting. Secure Firewall obtains the latest fingerprints through the Vulnerability Database (VDB) package update. In the advanced settings section of an access control policy, you can find many modern techniques to handle encrypted traffic.
Leave a Reply