Best Practices for Traffic Decryption
Enabling traffic decryption functionality introduces additional CPU overhead, which can impact the overall throughput of the system. Therefore, you should consider the following best practices when you configure an SSL policy:
- SSL rules are evaluated in top-to-bottom order. Place the SSL rules with Block and Do Not Decrypt actions before the rules that have Decrypt Known Key and Decrypt Resign actions.
- When you add SSL policy rules, place the rules with specific conditions before the rules with broader conditions. In general, rules that require the least amount of information to determine the outcome should be placed closer to the top of the SSL policy rule base.
Configuring a Decryption Policy
In the following sections, you learn how to configure an SSL policy to decrypt network traffic, and then enable a next-generation security policy, such as a file policy, to analyze the decrypted traffic further. You begin the process by creating public key infrastructure (PKI) objects. Next, you configure an SSL policy using the PKI objects. To demonstrate the benefits of traffic decryption, you can also create or reuse a file policy. Alternatively, an intrusion policy could be used to show deep packet inspection. Finally, you must associate your SSL policy with the access control policy that you intend to deploy to your threat defense.
Figure 18-9 summarizes the steps to implement traffic decryption functionality on Secure Firewall.
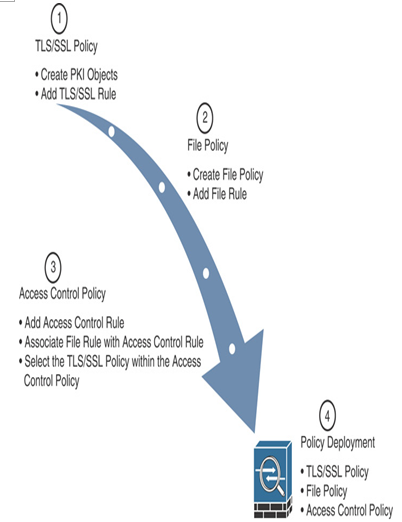
Figure 18-9 Steps to Implement Decryption with Next-Generation Security
PKI Objects
In an SSL policy, you use a combination of PKI objects and standard objects to establish the matching criteria for SSL rules. PKI objects can represent your internal public key infrastructure components. Before you create an SSL policy, add the following types of PKI objects by navigating to Objects > Object Management.
Internal CAs Object
The internal certificate authority object represents the certificates from internal CAs that you control. When you invoke this object in an SSL policy rule and select the Decrypt – Resign action, Secure Firewall uses the internal CA certificate object to re-sign the server certificate that is passed to the client from the external server the client wants to communicate with. It enables Secure Firewall to decrypt matching outgoing traffic and re-encrypt traffic that passes inspection to its destination.
To configure a self-signed Internal CAs object, use the following steps:
Step 1. Go to Objects > Object Management.
Step 2. On the left panel, select PKI > Internal CAs, as shown in Figure 18-10.
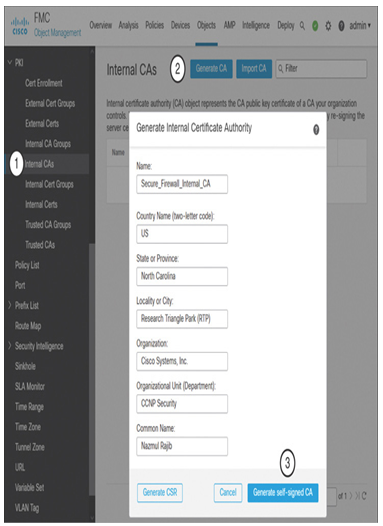
Figure 18-10 Generation of Internal Certificate Authority
Step 3. Click the Generate CA button.
Step 4. Complete the form with necessary information.
Step 5. Click the Generate Self-Signed CA button.
Leave a Reply