File Policy
Creating a file policy is not a requirement for traffic decryption; however, it allows you to experience the benefits of decryption. For example, if a file policy is deployed to block executable (EXE) files, but there is no SSL policy deployed on Secure Firewall, you can still transfer over protocols that support file transfers. In this case, the file policy is rendered ineffective because encryption prevents the access control policy rules from being able to evaluate the traffic. However, when an SSL policy is enabled to decrypt traffic and a file policy is also deployed to block file downloads, Secure Firewall can precisely block the transfer of files. The “Verification” section later in this chapter demonstrates this operation in detail, but for now, just configure a simple file policy to block the executable files, as shown in Figure 18-17. This figure shows the file rule condition only; however, the step-by-step instructions on File Policy configuration are described in Chapter 16, “Malware and File Policy.”
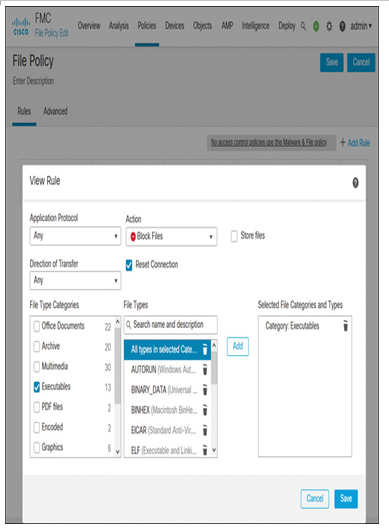
Figure 18-17 File Rule to Block the Transfer of Any Executable Files
Access Control Policy
After you configure an SSL policy and a file policy, you must invoke them in the access control policy you intend to use. You can modify an existing access control policy by navigating to Policies > Access Control or create a new one if existing policies do not meet your needs. After you enter the access control policy editor, complete the following steps to invoke the file policy and SSL policy:
Step 1. Click the Add Rule button to create an access control rule to match the source and destination of the encrypted sessions. Alternatively, you can modify an existing access control rule that matches the encrypted traffic.
Step 2. On the rule configuration window, select the Allow action and define all the matching conditions for the rule.
Step 3. On the Inspection tab, select the File Policy you created in the previous section (see Figure 18-18). This is the place to map a file policy with the matching traffic.
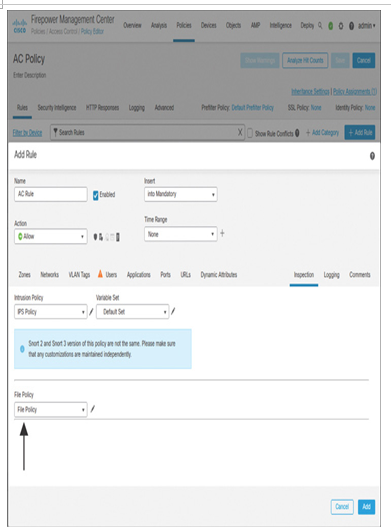
Figure 18-18 Mapping a File Policy with Matching Traffic
Step 4. On the Logging tab, enable Log at the End of Connection. This option allows you to see connection events when the rule matches traffic.
Step 5. Click the Add button on the rule configuration window. The GUI returns to the access control policy editor page.
Step 6. On the access control policy editor, you will find a link to the currently selected SSL policy. If this is a new configuration, the link is SSL Policy: None. Click the None link. This opens a pop-up window that displays a list of the available SSL policies, as shown in Figure 18-19.
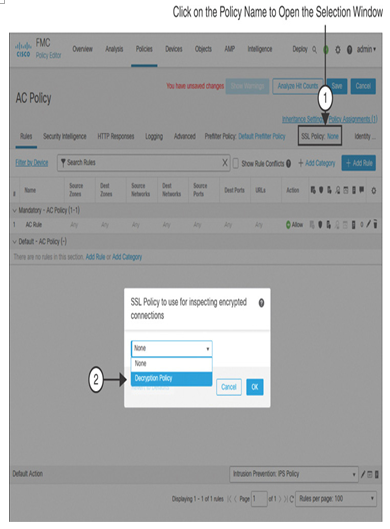
Figure 18-19 Invoking an SSL Policy into an Access Control Policy
Step 7. Use the drop-down to select the SSL policy you created earlier. After it is selected, click the OK button to return to the policy editor page.
Step 8. Click Save on the access control policy editor page to save the configurations.
Step 9. Navigate to Deploy > Deployment. Deploy the policies to your threat defense.
Leave a Reply