Internal Certs Object
The internal certificate object represents the certificates of servers that your organization administers. To configure an internal certificate object, you upload the server certificate and private key. When you invoke this object in an SSL rule and select the Decrypt – Known Key action, Secure Firewall uses the uploaded private key to decrypt any matching incoming traffic.
To configure an Internal Certs object, use the following steps:
Step 1. Go to Objects > Object Management.
Step 2. On the left panel, select PKI > Internal Certs, as shown in Figure 18-11.
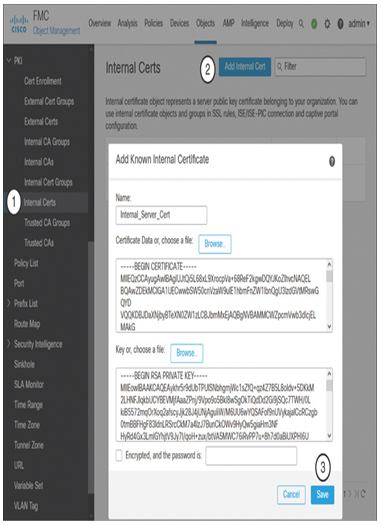
Figure 18-11 Addition of a Known Internal Certificate
Step 3. Click the Add Internal Cert button.
Step 4. Click the Browse buttons to upload the certificate and key files of your internal web server.
Step 5. Click the Save button.
SSL Policy
After you create the necessary PKI objects, you can create an SSL policy by using the following steps:
Step 1. On the management center, navigate to Policies > Access Control > SSL. The SSL policy configuration page appears.
Step 2. To create a new policy, click the New Policy button. The New SSL Policy configuration window appears (see Figure 18-12).
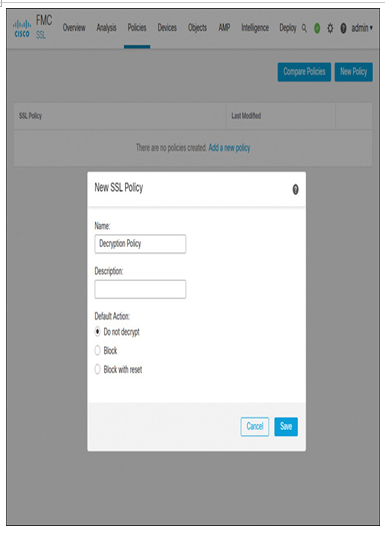
Figure 18-12 New SSL Policy Configuration Window
Step 3. Give a name to the policy and select Do Not Decrypt as the default action. The option you select for the default action is used to handle the traffic that does not match any SSL rules. Click the Save button to save the policy. The new policy opens in the SSL policy editor.
Step 4. In the policy editor page, click the Add Rule button. This opens the Add Rule configuration window. On this window, you define your SSL rule matching conditions and rule action.
Step 5. Name the SSL rule, define the direction of the encrypted traffic, and select an action and PKI object based on the traffic direction. For example:
- Select the action Decrypt – Resign for the outgoing traffic, which will flow from inside to the outside zone. Then select an Internal CA object (see Figure 18-13).
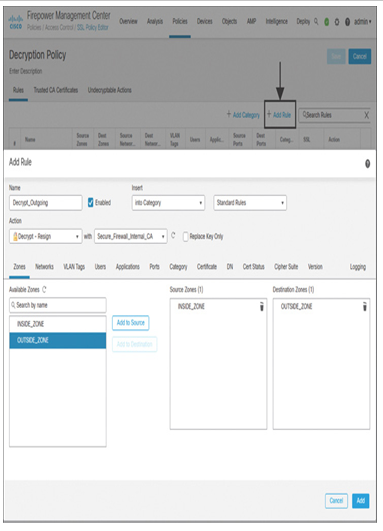
Figure 18-13 SSL Rule with the Decrypt – Resign Action Matching Outbound Traffic
- Select the Decrypt – Known Key action to handle incoming traffic, which will flow from the outside zone to the internal zones. Then select an Internal Cert object (see Figure 18-14).
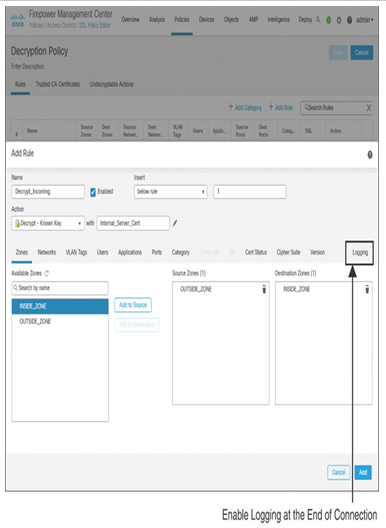
Figure 18-14 SSL Rule with the Decrypt – Known Key Action Matching Inbound Traffic
Step 6. Optionally, for all SSL rules, enable logging for matching encrypted traffic. In the Add Rule window, go to the Logging tab and select Log at the End of Connection to enable logging for matching encrypted connections. After you complete the logging configuration, click the Add button to create the SSL rule. The GUI returns to the SSL policy editor page.
Step 7. Similarly, you can enable logging for any traffic that can match the default action. On the policy editor page, click the logging icon next to the drop-down for default action, as shown in Figure 18-15.
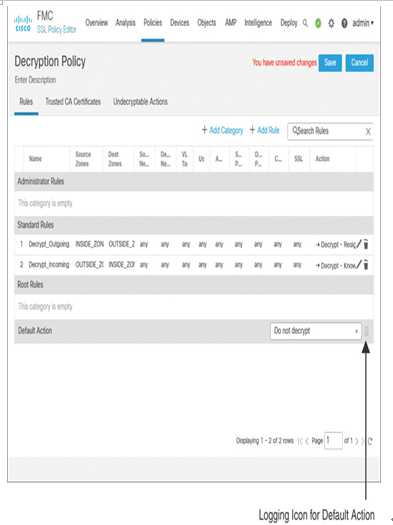
Figure 18-15 Configuration of SSL Rules to Match Traffic from Both Directions
Step 8. Finally, define how Secure Firewall will handle the undecryptable traffic. Navigate to the Undecryptable Actions tab and modify the selections using the drop-down as desired. For example, if you do want to deny any SSLv2 traffic, you can select Block action from the drop-down, as shown in Figure 18-16. After the desired changes are made, save the configurations.
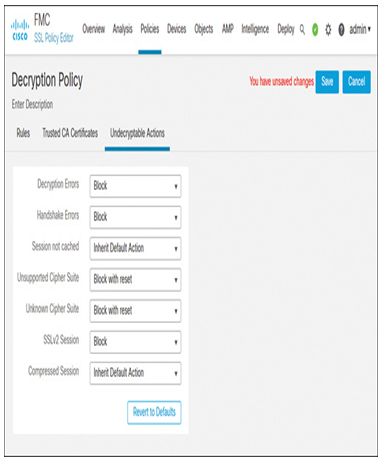
Figure 18-16 Actions for Undecryptable Traffic
Leave a Reply