Remote Access VPN
In a remote access virtual private network, an endpoint device located in a remote network can connect to an organization’s internal network over the Internet via a secure channel. The endpoint device uses Cisco AnyConnect Secure Mobility Client to establish a secure tunnel with a threat defense, which is deployed in an organization network as a remote access VPN headend. The AnyConnect client supports Windows, Mac, Linux, Apple iOS, and Android operating systems. Therefore, you can use your laptop, smartphone, or tablet as an endpoint device to connect to your organization’s network remotely via a secure tunnel.
Figure 19-6 shows a high-level design of a remote access virtual private network.
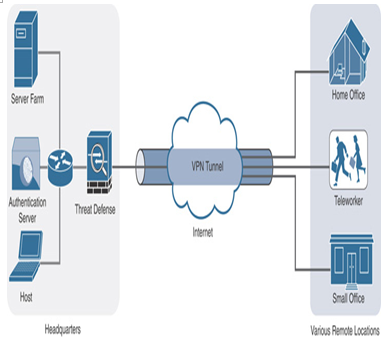
Figure 19-6 Remote Access VPN Topology
Note
In this chapter, the terms VPN gateway, VPN headend, VPN peer, and VPN device refer to the Cisco Secure Firewall Threat Defense with VPN services enabled.
IPsec Essentials
Internet Protocol Security (IPsec) is not a single networking protocol. It encompasses a group of protocols and algorithms that work together to establish a secure connection over the public Internet. The Internet Engineering Task Force (IETF) defines the standards for implementing IPsec using three distinct protocols: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE). Figure 19-7 displays the major components that are used to establish an IPsec tunnel, and Table 19-2 delineates their security functions.
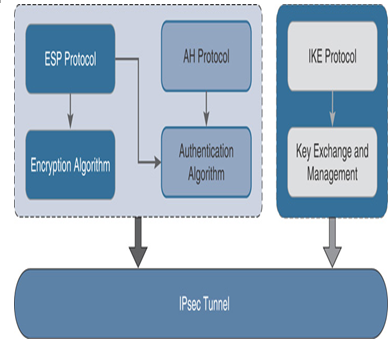
Figure 19-7 Major Protocols Used to Build an IPsec Tunnel
Table 19-2 Three Major Security Protocols of the IPsec Framework
| Protocol Name | Functions | Protocol/Port Number | References |
| Authentication Header (AH) | Integrity, authentication, anti-replay | IP Protocol 51 | RFC 4302 |
| Encapsulating Security Payloads (ESP) | Confidentiality, integrity, authentication, anti-replay | IP Protocol 50 | RFC 4303 |
| Internet Key Exchange (IKE) | Key exchange | UDP 500 | RFC 7296 |
As the technologies are evolving fast, and modern computers are coming up with higher computational power, attackers are able to break the older algorithms. Therefore, it is critical to consider the stronger algorithms when implementing an IPsec tunnel. Cisco regularly reviews the vulnerabilities and weaknesses of protocols, and it stops supporting the less secure ciphers and algorithms in Secure Firewall. For example, from Version 6.7 or higher, Secure Firewall does not support the 3DES, AES-GMAC, AES-GMAC-192, and AES-GMAC-256 encryption algorithms. The only exception in supporting weaker encryption algorithms is DES. Secure Firewall allows you to enable the DES algorithm in Evaluation Mode or in a deployment without export-controlled licenses. Table 19-3 provides some examples of cryptographic algorithms to strengthen the security of a tunnel.
Table 19-3 Cryptographic Algorithms and Their Strengths
| Purpose | Cryptographic Algorithm | Reference | Key Strength |
| Encryption | Advanced Encryption Standard (AES) | FIPS 197 | AES256 |
| Data Encryption Standard (DES) | FIPS 46-3 | 3DES (Triple DES) | |
| Integrity | Secure Hash Algorithm (SHA) | FIPS 180-4 | SHA-2 with 512-bit digest |
| Message-Digest Algorithm | RFC 1321 | MD5 | |
| Key Exchange | Diffie-Hellman (DH) Key Agreement Algorithm | RFC 3526 | DH Group 14 (2048-bit modulus) |
| Elliptic-Curve Diffie-Hellman (ECDH) | RFC 5903 | DH Group 21 (521-bit random elliptic curve) |
Caution
The stronger the algorithm you implement, the higher the CPU utilization would be on a threat defense. Therefore, when selecting a threat defense model for your network, you must carefully consider your throughput requirements and compare the maximum limits with the specifications provided in the product datasheet (published at cisco.com).
Leave a Reply