Mode of Operation
An IPsec tunnel between two VPN gateways can operate in two modes:
- Transport mode: In this mode, only the payload is encrypted or authenticated. The original IP header remains unmodified and unencrypted.
- Tunnel mode: In this mode, the entire packet (IP header and payload) is encrypted, authenticated, and then encapsulated into a new IP packet, which uses a new IP header.
You can configure the VPN peers with the AH or ESP protocol individually (such as only the AH protocol or only the ESP protocol), or in combination with both AH and ESP protocols at the same time. For example, Figure 19-8 shows the insertion of authentication header in both transparent mode and tunnel mode. In transport mode, an authentication header is inserted after the original IP header of a packet and before the next layer protocol (such as TCP, UDP, or ICMP). In tunnel mode, the original IP header is encapsulated by a new IP header and an authentication header. Similarly, Figure 19-9 shows the insertion of the ESP header in both modes, and Figure 19-10 shows the insertion of both AH and ESP headers together at the same time.
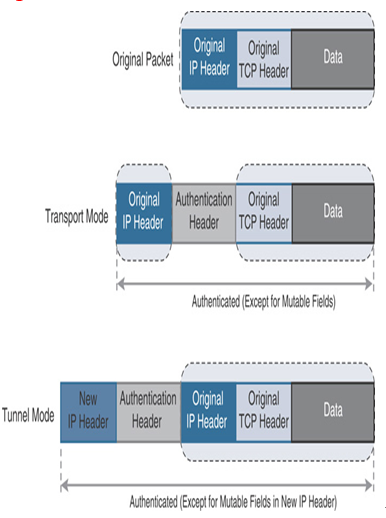
Figure 19-8 An Authentication Header (AH) in an IPv4 Packet
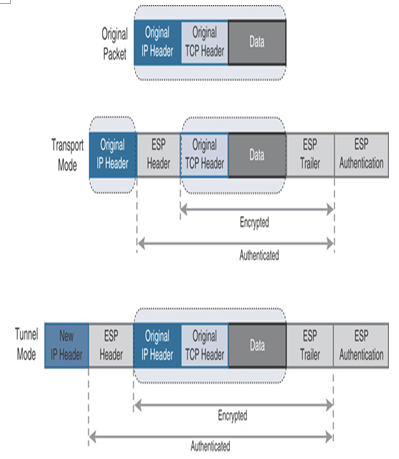
Figure 19-9 An Encapsulating Security Payload (ESP) Header in an IPv4 Packet
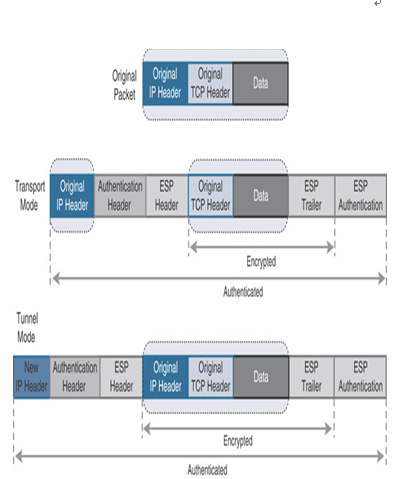
Figure 19-10 Encapsulation of AH and ESP Headers Simultaneously
Security Association and Key Exchange
To establish an IPsec tunnel, the VPN peers exchange a proposal of various security protocols and algorithms that they can support. This proposal is known as a transform set. Depending on your organization’s security policy, you can combine the desired security attributes in the proposal. After negotiating a proposal, VPN peers establish a security association (SA) between them. Establishment of a security association indicates that the VPN peers have agreed on the security attributes that they will use to protect user data. To build a security association and exchange secret keys, VPN peers use the Internet Key Exchange (IKE) protocol and Internet Security Association and Key Management Protocol (ISAKMP) framework. Figure 19-11 shows an example of proposing various security attributes in the transform set. This packet is captured during an IKE protocol negotiation between two VPN peers and then analyzed in a packet analyzer.
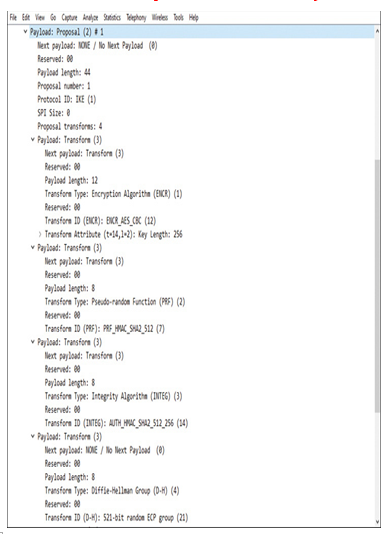
Figure 19-11 Proposal of Security Protocols and Algorithms in a Real Packet
The IKE protocol has been enhanced significantly since its first implementation, IKEv1. The new version of IKE—called IKEv2—introduces stronger security features and offers additional reliability, resiliency, and efficiency (see RFC 7296 for detail). The operations of IKEv1 and IKEv2 are also different. The following sections discuss the steps of IKE operations in both versions.
IKEv1
The IKEv1 negotiations between two VPN peers complete in two phases:
- IKEv1 Phase 1: In this phase, both VPN peers authenticate each other and establish a security association to perform an IKE operation. Phase 1 allows the peers to communicate securely in phase 2.
IKE phase 1 can operate in two modes: main mode and aggressive mode. The main mode exchanges six messages to complete its operation, whereas the aggressive mode can complete its operation in three messages. Although the aggressive mode is faster, the main mode is more secure.
- IKEv1 Phase 2: In this phase, both VPN peers use the secure communication channel that was established in phase 1 to negotiate security associations for IPsec operation. IKE phase 2 operates only in one mode, known as quick mode.
Figure 19-12 shows various phases to establish and terminate an IPsec tunnel.
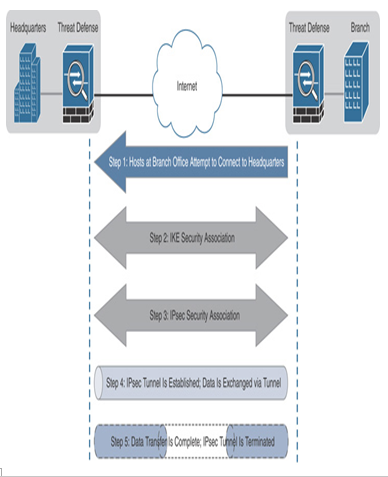
Figure 19-12 IPsec Tunnel Creation and Termination
Leave a Reply