Authentication
During the IKE negotiation process, the VPN peers can authenticate each other by using preshared keys. Preshared keys are simple to configure and feasible to deploy in a smaller network. However, they are not scalable in a large VPN deployment. For scalability, you can use digital certificates. The VPN peers can obtain digital certificates from the certificate authority (CA) of a public key infrastructure (PKI) system. A CA is responsible for signing and issuing digital certificates, which are used to validate the identity of the VPN peers. In the real world, you do not want a threat defense to serve as a certificate authority; instead, you enroll the participating threat defense devices with a certificate authority server. Upon a successful certificate enrollment, the threat defense devices—the VPN peers—exchange their identity certificates to validate each other.
Figure 19-15 shows the communications between a certificate authority and the threat defense in a PKI.
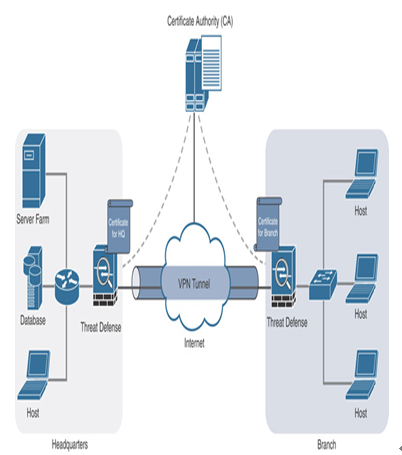
Figure 19-15 Secure Firewall in a Public Key Infrastructure (PKI)
Additionally, the IKEv2 protocol includes support of the Extensible Authentication Protocol (EAP) authentication framework to authenticate the IKE SAs. The authentication methods in EAP-IKEv2 protocol are based on asymmetric key pairs, passwords, and symmetric keys.
Site-to-Site VPN Deployment
The following sections describe how to implement the site-to-site VPN using Secure Firewall.
Prerequisites
Before you begin the core configuration of the site-to-site VPN, fulfill the following prerequisites:
- When registering your management center with Cisco Smart Software Licensing, you must allow the export-controlled functionality, as shown in Figure 19-16. It allows you to enable strong cryptographic features on your Cisco Secure Firewall. If the export-controlled functionality is not allowed, you can use only the Data Encryption Standard (DES) algorithm to encrypt data. Likewise, if you run Secure Firewall in evaluation mode, DES is the only encryption algorithm you can implement.
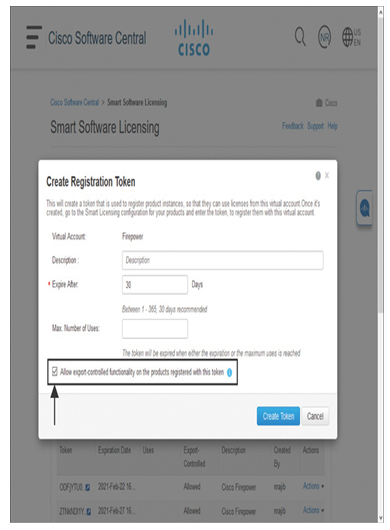
Figure 19-16 Allowing Export-Controlled Functionality
- In a site-to-site VPN network, two or more threat defense devices are connected to each other over the public Internet (see the examples of various VPN topologies in Figure 19-3, Figure 19-4, and Figure 19-5). This chapter uses the point-to-point network topology, illustrated in Figure 19-17, to demonstrate the configuration and operation of a site-to-site VPN. To emulate the headquarters and branch sites, additional threat defense devices are registered to the management center (see Figure 19-18). The device registration process is described step by step in Chapter 3, “Licensing and Registration.”
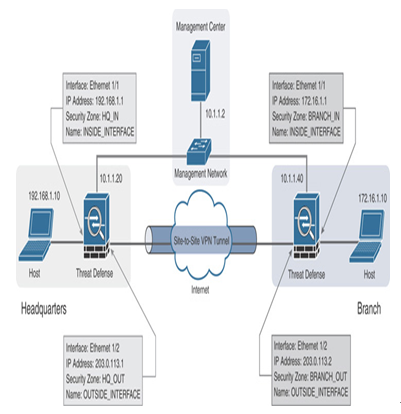
Figure 19-17 Lab Topology to Implement the Site-to-Site VPN Services
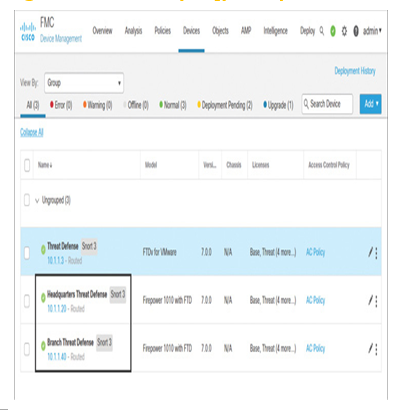
Figure 19-18 Registration of Multiple Threat Defense Devices with the Management Center
- After the threat defense devices are registered, configure the interfaces of both devices to match the settings on the topology diagram in Figure 19-17. Figure 19-19 shows the configurations of both threat defense devices located at headquarters and branch sites.
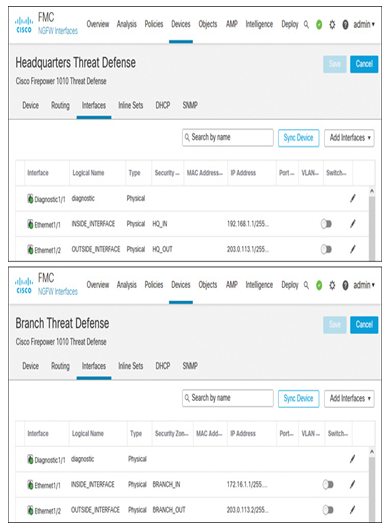
Figure 19-19 Interface Configurations of a Threat Defense
- Create network objects for the headquarters and branch networks. You can create them by navigating to Objects > Object Management before you configure the VPN topology. Alternatively, you can add the objects on the fly when you are on the VPN configuration wizard. Figure 19-20 shows two custom network objects to represent the local-area networks (LANs) of headquarters and branch sites.
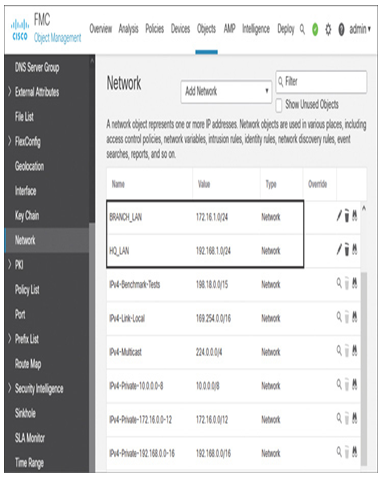
Figure 19-20 Network Objects for Headquarters and Branch Networks
Leave a Reply